In today’s digital world, security is more important than ever. With so much of our personal and professional lives taking place online, it’s essential to have strong protections in place to defend against cyberattacks. One way to do this is through Multifactor Authentication (MFA).
You might be wondering what all the hype about MFA is about. After all, isn’t a username and password enough to keep your accounts secure? Unfortunately, no.
Passwords are becoming increasingly easy for hackers to obtain. Therefore, MFA has become such an important security measure. Instead of relying on a single password, multi-factor authentication uses a combination of factors to verify your identity.
While MFA can add an extra step to the login process, it’s well worth the effort to keep your data safe. But what is multi-factor authentication, and how does it work? Read on to find out.
Table of Contents
ToggleWhat Is Multi-Factor Authentication (MFA)?
Traditionally, all you needed to log into your online accounts was a username and password. In today’s cybersecurity and anti-fraud landscape, that’s simply not enough since these two factors are easy to crack. Therefore, all online service providers require an additional factor of authentication, which is where MFA comes in.
Multi-factor authentication is a method of identity verification that requires using more than one factor to authenticate a user. The most common type of MFA uses three factors: something you know (like a password), something you have (like a phone), and something you are (like your fingerprint or face).
The main purpose of multifactor authentication is to create an extra defence layer that makes it more difficult for unauthorised individuals to access a given target. The target could be a computing or mobile device, a database network, or a physical location. If an unauthorised party manages to bypass one authentication factor, one more barrier will prevent them from accessing your data.
What is Adaptive Multi-Factor Authentication (AMFA)
In response to evolving cyber threats, Adaptive Multi-Factor Authentication (AMFA) provides a dynamic approach to identity verification. Unlike static MFA methods, AMFA adjusts authentication requirements based on real-time risk assessment and contextual factors.
Key features of AMFA include:
- Risk-based authentication: AMFA evaluates each login attempt’s risk level and adapts authentication accordingly, ensuring higher security for high-risk activities.
- Continuous monitoring: AMFA continuously monitors user sessions for anomalies, enabling real-time threat detection and mitigation.
- Integration with behavioral analytics: By analyzing user behaviour patterns, AMFA detects deviations that may indicate fraudulent activity, enhancing security.
- User-friendly experience: AMFA balances security and usability, sparing legitimate users unnecessary authentication hurdles while maintaining robust protection.
In summary, AMFA offers a responsive and user-friendly solution to cybersecurity challenges, strengthening defenses in today’s digital landscape.
Why is Multi-Factor Authentication important?
A recent dark web audit revealed that cybercriminals have 15 billion login credentials, which they have obtained from 100,000 security breaches. With so many credentials to choose from, your company private records, healthcare records, or bank account could be at risk. That’s basically why you need multi-factor authentication.
But that’s not all. Password reuse is also a huge problem. It’s not uncommon for people to use the same password for different accounts. While this might make it easier to remember your login details, it makes it much easier for fraudsters to break into your accounts.
Research shows that 81% of confirmed data breaches involve weak, default, or stolen passwords. This is where MFA comes in. Using multiple authentication factors, you can make it much harder for hackers to access your accounts since they would need more than just your password.
MFA is a bulletproof authentication process, which makes it vital in a world where fraud threats are increasing every minute. It will add another security layer to ensure that your data is safe from attacks that could have costly consequences.
How does Multi-Factor Authentication work?
When you enable MFA on an account, you’ll be prompted to enter not just your username and password but also a second factor, as a password isn’t needed then this is second factor authentication would be completed through the method of Passwordless Authentication.
This second factor could be a code sent to your phone via text or an authenticator app like Google Authenticator. It could also be a biometric factor like your fingerprint or facial recognition, known as Biometric Authentication.
If you’re using an authenticator app, you’ll open the app and enter the code that’s displayed. These codes are one-time passwords (OTPs) that are only valid for a few seconds.
The codes make it impossible for someone to hack your account. Even if they have your password, they won’t be able to generate the correct code in time.
Once you’ve entered the username, password, and second factor, you’ll be logged into your account. The process might take an extra minute, but it’s a small price to pay for the added security that MFA provides.
Best practices for setting up Multi-Factor Authentication
Implementing Multi-Factor Authentication (MFA) is essential for robust security measures. Here are some best practices to ensure effective setup and management:
Create user roles:
Define user roles within your organization and assign appropriate access levels. Different roles may require different authentication methods and levels of authorization.
Create strong password policies:
Enforce strong password policies to complement MFA. Require passwords to be complex, regularly updated, and not reused across multiple accounts.
Rotate security credentials:
Regularly rotate security credentials, such as passwords, tokens, and encryption keys, to minimize the risk of compromise. Set up automated systems to facilitate this process.
Follow least privilege policy:
Adhere to the principle of least privilege by granting users only the permissions necessary to perform their job functions. Restrict access to sensitive data and systems to minimize potential security breaches.
Implement adaptive authentication:
Utilize adaptive authentication techniques to dynamically adjust authentication requirements based on contextual factors such as user behavior, location, and device characteristics.
Monitor and audit access:
Continuously monitor user access and authentication events to detect anomalies or suspicious activities. Conduct regular audits to ensure compliance with security policies and identify areas for improvement.
Provide user education and training:
Educate users about the importance of MFA and how to use it effectively. Offer training sessions on recognizing phishing attempts, securing devices, and protecting sensitive information.
Use Multi-Factor Authentication everywhere possible:
Extend MFA protection beyond traditional login scenarios to cover critical systems, applications, and cloud services. Implement MFA for all privileged accounts and administrative access.
Employ biometric authentication:
Consider incorporating biometric authentication methods such as fingerprints, facial recognition, or iris scans for added security and user convenience.
Regularly update MFA solutions:
Stay informed about updates and patches for your MFA solutions to address vulnerabilities and ensure optimal performance. Regularly review and update your MFA strategy to adapt to evolving security threats and technological advancements.
By following these best practices, organizations can enhance their security posture and protect sensitive data and resources effectively with multi-factor authentication.
Examples of Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) employs a combination of authentication factors to enhance security. Here are some common examples:
Remote access for employees:
MFA adds extra security for remote employee access, ensuring only authorized personnel can log in, regardless of location.
System access for on-site employees only:
MFA heightens security for on-site employees accessing sensitive systems, allowing only authorized personnel within the workplace to log in, bolstering data protection.
VPN access:
Employees connecting to the company network via Virtual Private Network (VPN) often require MFA, ensuring secure remote access.
Email platforms:
MFA safeguards email accounts from unauthorized access, commonly used in platforms like Gmail, Outlook, or corporate email systems.
Financial transactions:
MFA secures online banking, cryptocurrency exchanges, and payment platforms, protecting financial assets and transactions.
Government systems:
MFA secures access to sensitive government databases and portals, ensuring only authorized personnel can access confidential information.
Customer portals:
Many online services and e-commerce platforms offer MFA to enhance customer account security, protecting personal information and transactions.
Social media platforms:
MFA adds an extra layer of security to social media accounts, preventing unauthorized access and safeguarding personal data.
Cloud storage services:
MFA is commonly used to protect files and documents stored in cloud platforms like Dropbox, Google Drive, and OneDrive.
These examples demonstrate the versatility of multi-factor authentication, combining different factors to create robust security measures for various applications and user preferences applied across industries and platforms to mitigate the risk of unauthorized access and data breaches.
Types of Multi-Factor Authentication methods
Different applications or online accounts will ask you for different types of MFA, depending on the sensitivity of the protected information. The most common types of MFA are:
Password or PIN (Knowledge)
This is the most basic type of MFA, and it’s also the type that most people are familiar with. When you set up an account, you’re asked to create a password or PIN. This is considered your first factor of authentication since it’s something that only you know.
Badge or smartphone (Possession)
In possession-based authentication, you need something on you, such as a badge or smartphone, to log into your account.
If you’re using a badge or smart card, you’ll need to swipe it or insert it into a card reader. The badge contains a chip that houses your account information. When you swipe the badge, the reader will access your account and log you in.
If you’re using a smartphone, you’ll need to download an authentication app like Google Authenticator. These apps generate codes that change every few seconds. This code is known as a time-based one-time password (TOTP) and changes every 30 seconds.
Biometric data (Inherence)
This type of MFA uses your physical characteristics, such as your fingerprint, earlobe geometry, voice authentication, iris, or facial recognition, to verify your identity.
For instance, if you’re using facial recognition, you’ll place your face in front of the camera on your smartphone. The camera will read your facial biometrics and compare them to the stored template. If the two match, you’ll be logged into your account.
Other types of Multi-Factor Authentication
In addition to the common MFA methods mentioned, there are other innovative approaches to authentication:
Adaptive authentication or risk-based authentication
This method evaluates various risk factors, such as the user’s behavior, location, device, and login context, to dynamically adjust authentication requirements. It allows for a more tailored and adaptive approach to security.
Location-based authentication
This method verifies the user’s identity based on their geographical location. If the login attempt occurs from an unfamiliar or suspicious location, additional authentication steps may be required to ensure security.
Token-based authentication
Token-based MFA involves using physical or software-based tokens to generate one-time codes. These codes are then entered along with the username and password during the login process, adding an extra layer of security.
Geolocation authentication
Geolocation MFA verifies the user’s identity based on their physical location. If the user attempts to log in from a location that is not recognized or falls outside predefined parameters, additional authentication measures may be triggered.
Push-based authentication
With push-based MFA, the user receives a push notification on their registered device when attempting to log in. They can then approve or deny the login attempt directly from the notification, adding convenience without compromising security.
These additional types of multi-factor authentication offer organizations flexibility in choosing the most suitable authentication methods based on their security needs and user preferences.
In which businesses can MFA be used?
You can use multi-factor authentication in any business where security is a concern. This includes businesses in industries such as:
● Gaming
● Cryptocurrency
● Insurance
● Finance
● Healthcare
Using MFA in these industries protects user accounts and prevents fraud. MFA ensures that users are who they say they are when making transactions or requesting access.
For instance, in insurance, you can use MFA to verify the identity of policyholders when they’re logging into their accounts to make a claim. In finance, MFA can be used to verify the identity of customers when they’re logging into their bank account or making an online purchase.
What are the differences between MFA and Two-Factor Authentication (2FA)?
MFA and Two-Factor Authentication (2FA) are similar in that they both require the use of more than one factor to verify your identity. The main difference between MFA and 2FA is the number of forms of identification required.
2FA is a type of MFA that requires 2-step verification when accessing an account. It requires the user to use two authentication factors. These could be your password and an additional factor like soft token or biometrics.
With MFA, you’re required to use at least two authentication factors. These could be your password, a one-time password (OTPs), and biometrics. As you can see, all 2FAs are MFAs, but not all MFAs are 2FAs.
So, which is better? MFA or 2FA?
There is no clear answer, as both have their own advantages and disadvantages. MFA is generally seen as more secure, as it is harder for someone to access all the necessary information.
The benefits of Multi-Factor Authentication (MFA)
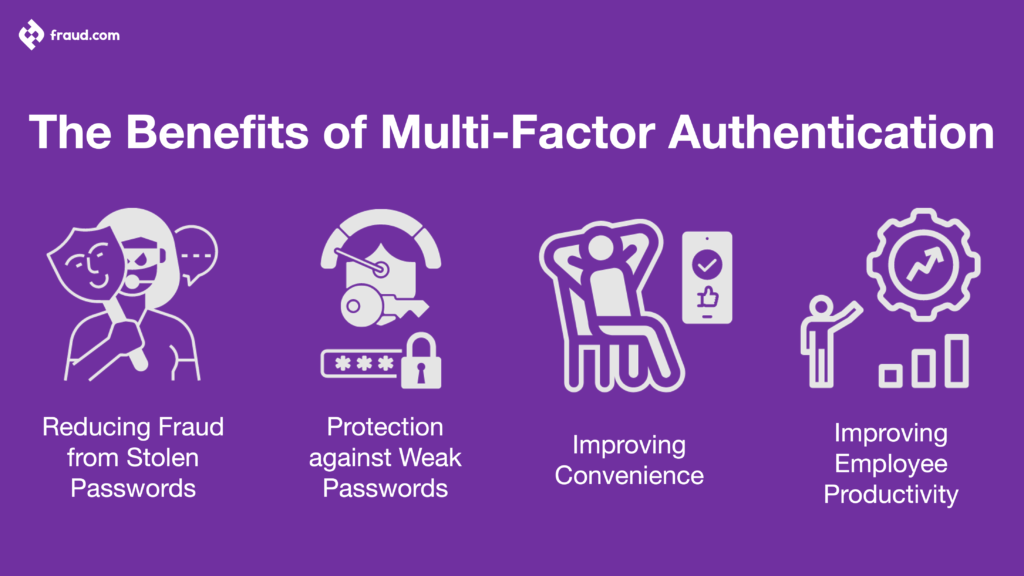
Multi-factor authentication provides several benefits over single-factor authentication. These benefits include:
Reducing fraud from stolen passwords: It’s easy for hackers to get your password through methods like phishing and keylogging. However, it’s much harder for them to get your second authentication factor. This means that MFA can help to reduce the chances of fraudsters being able to access your account and commit fraudulent activities like identity theft.
Protection against weak passwords: Even if your password is weak, MFA can help to protect your account if your second authentication factor is strong. This means that you don’t have to worry as much about choosing a strong password, as the second factor will make it more difficult for hackers to access your account.
Improving convenience: Multi-factor authentication technology doesn’t have to be inconvenient. In fact, many MFA methods are more convenient than single-factor authentication. For example, soft tokens can be generated on your smartphone, and biometrics can be used to quickly and easily verify your identity.
Improving employee productivity: By making it more difficult for hackers to gain access to accounts, MFA can improve employee productivity. Employees won’t have to waste time resetting passwords and dealing with the consequences of a security breach. They will also have more peace of mind, knowing that accounts are better protected, also leading to less customer friction.
Our Multi-Factor Authentication solution – Udentify
Our article answers any questions you may have about why you need multi-factor authentication. Now it’s time to ask yourself why you don’t have MFA set up for your accounts. If you’re ready to take your security to the next level using MFA, start with Udentify.
Udentify protects your online accounts by providing six layers of security with a leading identity verification and authentication system. Our solution deters fraudsters by authenticating only the right person using voice and face biometrics and liveness detection.
You don’t have to worry about user experience because we offer passwordless authentication and passive liveness detection. This means you don’t have to memorise a string of characters or perform uncomfortable gestures to verify identity.
Visit our website to learn more about Udentify and how it can benefit you and your company!
MFA FAQs
| MFA FAQs | Answers |
|---|---|
| What is Multi-Factor Authentication? | Multi-Factor Authentication (MFA) is a security method that requires multiple forms of verification to access an account or system. |
| Why is Multi-Factor Authentication important? | MFA adds an extra layer of security, making it much harder for hackers to access accounts, especially in a world where password breaches are common. |
| How does Multi-Factor Authentication work? | MFA requires users to provide two or more authentication factors, such as a password and a code sent to their phone, before granting access to an account. |
| What are the best practices for setting up Multi-Factor Authentication? | Best practices include creating user roles, implementing strong password policies, rotating security credentials, and providing user education and training. |
| In which businesses can MFA be used? | MFA can be used in any business where security is a concern, including industries such as gaming, cryptocurrency, insurance, finance, and healthcare. |
| What are the differences between MFA and Two-Factor Authentication (2FA)? | While both require multiple factors for authentication, MFA typically requires at least two factors, while 2FA specifically requires two factors. |
| So, which is better? MFA or 2FA? | There’s no clear answer, as both have their own advantages and disadvantages. MFA is generally seen as more secure, but the choice depends on specific security needs. |
| What are the benefits of Multi-Factor Authentication (MFA)? | MFA reduces fraud from stolen passwords, protects against weak passwords, improves convenience, and enhances employee productivity by securing accounts effectively. |
| How can I implement Multi-Factor Authentication for my accounts? | You can implement MFA by choosing a reliable MFA solution provider like Udentify, which offers passwordless authentication and multiple layers of security. |
| Where can I learn more about Multi-Factor Authentication? | You can learn more about MFA by visiting the website of MFA solution providers like Udentify by fraud.com and exploring their resources and services. |









