Customer identity verification is more crucial than ever, especially in today’s fast-paced digital landscape. Businesses are continuously seeking solutions that not only streamline processes but also enhance security. Cloud KYC is a game-changing approach to identity verification that leverages the power of the cloud to make life easier for both companies and customers alike.
Imagine being able to verify your customer’s identity swiftly and securely without the hassle of traditional methods. Cloud KYC does just that by adopting cutting-edge technologies to ensure compliance while providing a seamless user experience. Whether you’re in finance, e-commerce, or any sector requiring robust authentication measures, understanding how cloud KYC works can transform your business practices.
Let’s dive deeper into what cloud KYC entails and explore its stages, components, regulatory implications, and much more!
Table of Contents
ToggleWhat is cloud KYC?
Cloud KYC, or Cloud Know Your Customer, represents a modern approach to digital identity verification. It shifts the traditional customer KYC processes from on-premise systems to cloud-based platforms. By utilizing advanced technologies like artificial intelligence and machine learning, cloud KYC enhances accuracy in verifying customer identities.
The beauty of this system lies in its scalability. Companies can adapt their verification processes as they grow or face new challenges without needing significant infrastructure changes. Additionally, cloud KYC facilitates easy integration with existing software solutions.
This flexibility means that organizations can focus more on serving their customers rather than getting bogged down by manual verifications or outdated methods. In essence, it’s a powerful tool for enhancing security while streamlining operations in an increasingly digital world.
How does cloud KYC work?
Cloud KYC (Know Your Customer) solutions leverage advanced technologies, including AI, machine learning, OCR (optical character recognition), NFC (near-field communication), and liveness detection, to deliver secure, real-time identity verification services. Operating via scalable cloud infrastructure, these systems enable organisations to verify the identities of individual customers quickly and remotely while remaining compliant with evolving global regulatory standards, such as the Customer Identification Program (CIP), executive orders on ID verification, and proposed rules on AML compliance.
Key Stages of the Cloud KYC Process
- Data Ingestion & Customer Onboarding: Users initiate the onboarding process by submitting their personal and identity information, such as full name, date of birth, contact details, and biometric data, through digital channels. Cloud platforms streamline this entry using mobile apps and web interfaces, aligning with CIP requirements and executive compliance directives.
- Document Verification via OCR & NFC: The system validates government-issued identity documents (e.g. passports, driver’s licenses) by extracting data using OCR and verifying embedded chip data using NFC technology. These tools confirm document authenticity, ownership, and integrity while identifying tampering or forgery attempts by malicious cyber actors.
- Biometric Verification & Liveness Detection: Facial recognition systems combined with liveness detection ensures that the individual is physically present and matches the photo ID. These biometric checks, enhanced by behavioural analysis, help prevent spoofing and impersonation, reducing the risk of malicious cyber-enabled activity.
- Database Screening & Sanctions Checks: The system screens user identity data against global watchlists, politically exposed person (PEP) databases, and sanctions registries, including those published by the Bureau of Industry and Security. This step supports compliance with AML and counter-terrorism financing obligations while flagging high-risk individuals.
- Risk Scoring & Behavioural Analysis: AI-driven models evaluate behavioural patterns, device metadata, geolocation data, and data consistency to assign a fraud risk score. This helps identify anomalies linked to identity theft, synthetic identities, or the presence of malicious cyber actors.
- Continuous Monitoring & Adaptive Learning: Cloud KYC solutions continuously train large AI models on historical and real-time user data to enhance decision accuracy. Adaptive learning helps detect emerging fraud trends and reduce false positives, supporting future compliance with notice of proposed rulemaking and newly introduced KYC requirements.
- Regulatory Compliance & Automated Reporting: The platform ensures compliance with regional and international mandates, including Department of Commerce Infrastructure as a Service (IaaS) policies, CIP obligations, and executive orders on ID verification. Reports are automatically generated to support internal audits and external regulatory filings.
Cloud-based KYC solutions are redefining identity verification by combining speed, security, and regulatory alignment. These technologies not only help businesses verify the identities of legitimate customers but also fortify defences against fraud, enhancing trust and operational efficiency in the digital era.
Key stages of the Cloud KYC process
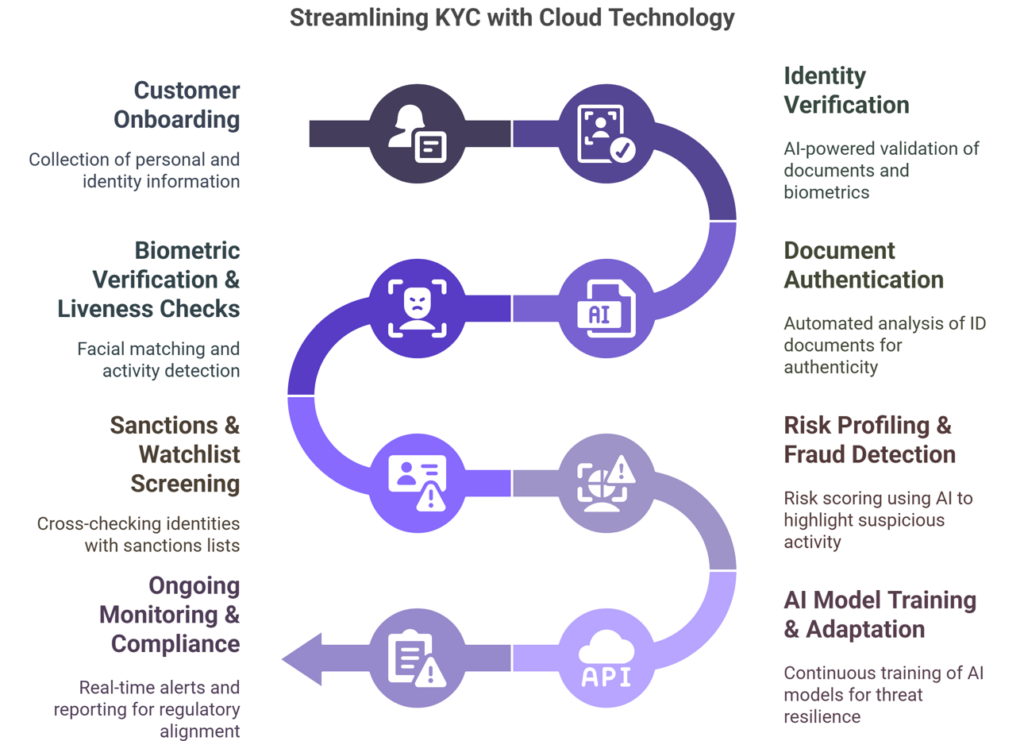
Here’s a clear breakdown of the full Cloud KYC lifecycle:
- Customer Onboarding: Collection of personal and identity information in compliance with the Customer Identification Program (CIP).
- Identity Verification: Use of AI-powered identity verification services to validate documents, biometrics, and personal data against secure databases.
- Document Authentication: Automated analysis of ID documents to confirm authenticity and detect forgery, aligned with standards set by the Bureau of Industry and Security.
- Biometric Verification & Liveness Checks: Facial matching and activity detection to prevent impersonation and stop malicious cyber-enabled activity.
- Sanctions & Watchlist Screening: Cross-checking identities with sanctions lists to detect politically exposed persons and malicious cyber actors.
- Risk Profiling & Fraud Detection: Risk scoring using AI to highlight suspicious activity and enforce anti-fraud policies.
- AI Model Training & Adaptation: Platforms continuously train large AI models to learn from new patterns and remain resilient to evolving threats.
- Ongoing Monitoring & Compliance: Real-time alerts and reporting to ensure alignment with current and upcoming proposed rules, such as those outlined in a notice of proposed rulemaking or executive orders.
What are the 3 main components of cloud KYC?
While cloud KYC systems often involve multiple interconnected processes, three core components form the foundation of effective identity verification in the cloud:
1. Data Collection
At the outset, organisations must gather accurate personal data from customers through secure digital channels. This typically includes identity documents, contact details, and biometric data collected via online forms, mobile apps, or integrated platforms. The quality and integrity of this data are critical to the success of downstream KYC processes.
2. Identity Verification
Once data is collected, the system verifies the customer’s identity by cross-referencing it against trusted databases, such as government-issued ID records, watchlists, or financial registries. Technologies like document verification, facial recognition, and liveness detection help ensure that the identity being presented is both real and belongs to the person submitting it.
3. Risk Assessment
This component analyses the potential risk associated with each customer. Machine learning and behavioural analytics detect anomalies, assess fraud potential, and flag suspicious profiles for further review. This stage supports ongoing due diligence and helps institutions meet regulatory obligations related to anti-money laundering (AML) and fraud prevention.
These three elements, data collection, identity verification, and risk assessment, form the core of most cloud KYC frameworks. Additional components such as customer due diligence (CDD), continuous monitoring, audit trails, and regulatory reporting often build upon this foundation to create a comprehensive compliance ecosystem.
What is the role of Cloud-based KYC solutions in modern identity verification?
Cloud-based KYC (Know Your Customer) solutions are transforming modern identity verification by offering scalable, secure, and compliant methods to authenticate customer identities in real time. These solutions leverage advanced technologies such as AI, machine learning, and biometric authentication to streamline the verification process, ensuring both efficiency and adherence to regulatory standards.
By utilizing cloud infrastructure, businesses can reduce onboarding friction while maintaining compliance with global regulations, including the Customer Identification Program (CIP), executive orders on ID verification, and proposed KYC rules. Cloud platforms provide scalable infrastructure as a service, enabling organizations to adapt quickly to fluctuating demands without compromising security.
Furthermore, cloud-based KYC platforms continuously evolve by learning from historical verifications and user behavior. This adaptive approach enhances fraud detection over time, reducing false positives and improving customer trust. As a result, organizations not only meet compliance obligations but also build secure, user-centric onboarding experiences across various sectors.
In summary, cloud-based KYC solutions are redefining modern identity verification by combining compliance, scalability, and intelligent threat detection in a single streamlined system.
Is cloud KYC a regulatory requirement?
Cloud-based KYC (Know Your Customer) solutions are not universally mandated by law; however, they have become instrumental in helping organisations comply with a complex and evolving global regulatory landscape. These solutions enable businesses to meet stringent identity verification and anti-money laundering (AML) requirements across various jurisdictions.
Key regulatory frameworks and authorities that organisations must consider include:
- United States: The Bank Secrecy Act (BSA) and oversight by agencies such as the Financial Crimes Enforcement Network (FinCEN) and the Securities and Exchange Commission (SEC) require financial institutions to implement effective KYC procedures to prevent money laundering and other financial crimes.
- United Kingdom: The Financial Conduct Authority (FCA) and the Prudential Regulation Authority (PRA) enforce regulations that mandate robust customer due diligence and identity verification processes to combat financial crime.
- European Union: The European Securities and Markets Authority (ESMA) and national Financial Intelligence Units (FIUs) oversee compliance with the Anti-Money Laundering Directive (AMLD) and the General Data Protection Regulation (GDPR), both of which set strict standards for customer identification and data protection.
- Global Standards: The Financial Action Task Force (FATF) provides international guidelines for AML and counter-terrorism financing (CTF), influencing national regulations and encouraging the adoption of effective KYC measures worldwide.
While cloud-based KYC solutions are not explicitly required by these regulations, they offer a practical and efficient means for organisations to achieve compliance. By leveraging cloud technology, businesses can implement scalable, secure, and real-time identity verification processes that align with regulatory expectations and enhance their ability to detect and prevent financial crimes.
In summary, adopting cloud-based KYC solutions enables organisations to proactively address regulatory requirements across multiple jurisdictions, streamline customer onboarding, and strengthen their overall compliance posture.
What is the cloud KYC rule?
The cloud KYC rule refers to the guidelines and regulations surrounding the use of cloud-based Know Your Customer processes. As businesses increasingly transition to digital platforms, these rules ensure that identity verification remains robust and compliant with legal standards.
Cloud KYC leverages advanced technologies for efficient data collection and analysis while maintaining user privacy. The rule mandates that companies must verify a customer’s identity, assess risks associated with money laundering or fraud, and adhere to local laws governing personal information.
By implementing cloud KYC solutions, organizations can streamline their compliance efforts. They benefit from quicker customer onboarding without sacrificing security or regulatory adherence. With ongoing developments in technology, it is essential for businesses to stay updated on cloud KYC regulations as they evolve alongside industry needs. Adapting swiftly ensures that your organization not only meets current requirements but also anticipates future challenges in identity verification.
Embracing Cloud KYC means more than just compliance; it’s about building trust with customers through secure practices tailored for today’s fast-paced digital landscape. This paves the way for seamless interactions between customers and businesses alike.
Streamlining digital onboarding and KYC compliance
Cloud-based KYC solutions streamline digital onboarding by automating identity verification while ensuring strict adherence to KYC compliance requirements. From the moment a user submits their identity information, cloud platforms begin real-time checks using advanced algorithms, biometric matching, and secure data validation processes.
By integrating KYC into the digital onboarding workflow, organisations accelerate customer acquisition without compromising regulatory obligations. These systems support global compliance frameworks and they also help detect and deter malicious cyber-enabled activity by identifying suspicious patterns and flagging potential malicious cyber actors early in the process.
Cloud infrastructure as a service allows companies to scale verification capabilities rapidly, whether onboarding hundreds or millions of users. Meanwhile, large AI models continuously learn from new data, improving fraud detection accuracy over time and reducing manual review burdens.
Ultimately, cloud-based KYC solutions allow businesses to verify the identities of individuals faster, meet compliance requirements confidently, and deliver secure, seamless onboarding experiences that meet the expectations of today’s digital-first customers.
Ready to transform your identity verification process?
Cloud-based KYC solutions are an essential tool for modern businesses aiming to stay ahead of compliance, fraud prevention, and user expectations. By embracing scalable, AI-powered cloud KYC systems, you can deliver secure, efficient, and regulation-ready onboarding experiences that meet the demands of today’s digital economy.
If you’re ready to explore how cloud KYC can enhance your customer verification processes, learn more about how our platform is redefining digital onboarding and identity compliance. Discover the tools, technologies, and strategies trusted by leading organisations worldwide to protect their platforms and build customer trust from the very first interaction.









