Application Fraud Detection
Our Application Fraud Detection Platform protects financial institutions by detecting sophisticated fraud such as synthetic identities, fraudulent addresses, and organized fraud rings at the application stage. Through its advanced rule engine and AI engine, it blocks suspicious applications. This not only reduces financial losses and increases operational efficiency but also ensures that legitimate applications are processed without delay.

Discover the Most Affordable
Application Fraud Prevention Solution.
What is the Application Fraud?
Application fraud is a widespread method of cyber fraud, prevalent in many sectors, especially finance and banking. In this type of fraud, individuals or groups apply for financial products using fraudulent or stolen data, such as identity, income, and address information. These applications can take various forms, such as account openings or credit card requests, and may include forged documents or manipulated information. Inadequate security measures at institutions allow this situation to lead to financial losses and legal problems.
Key Features
Our Application Fraud Detection Platform utilizes machine learning and data analysis to detect fraud early and accurately within application processes. Its key features include real-time detection, machine learning-powered analysis, comprehensive data integration, anomaly detection, a risk scoring system, customizable rules, detailed reporting, a user-friendly interface, and scalability. The platform is designed to enhance the security and profitability of businesses in sectors such as finance, e-commerce, telecommunications, insurance, and retail.
Real-Time Analysis
The moment applications enter the system, our advanced algorithms and AI-powered analysis engine are instantly activated. As a result, potential fraud risks are identified within seconds. This offers financial institutions the ability to make fast and accurate decisions, which both minimizes losses and increases operational efficiency.
Synthetic Identity Detection
By using advanced data analysis and artificial intelligence methods, we detect the origin of synthetic identities and their associated fraudulent information. This enables us to catch sophisticated types of fraud at the application stage—the kind that traditional systems often miss and have no real victim—thereby preventing financial losses.
Address and Information Verification
Information provided by applicants, such as addresses, phone numbers, and email addresses, is verified against trusted external databases and proprietary sources. This cross-check confirms the authenticity and consistency of the data, allowing potential fraud attempts and fraudulent identities to be identified during the application process.
Behavioral Analytics
By analyzing parameters such as form completion speed, device information, and IP address, our system identifies unusual behavioral patterns that may indicate non-human or fraudulent activity. This allows potential risks to be identified at the moment of application and either automatically blocked or flagged for further review.
Rule and AI Engine
Our solution combines flexible, continuously updated rule sets that track fraud trends with advanced machine learning models that learn from historical data. This hybrid approach provides instant protection against known fraud patterns while also offering the ability to automatically detect new and complex emerging threats. As a result, it reduces the workload for operational teams, minimizes financial losses, and ensures organizations always stay one step ahead.
Advanced Reporting and Alerting Systems
Our platform delivers comprehensive and detailed reports on detected fraud attempts. These reports help organizations understand fraud trends, while instant, automated alerts are sent to relevant departments, enabling a swift response. This process enhances the effectiveness of operational teams and minimizes financial losses.
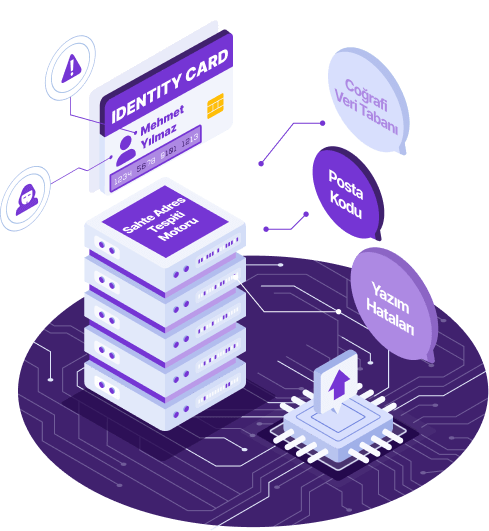
How Do We Detect Suspicious Applications?
Fraudsters often intentionally make minor changes or use typos in names and addresses to conceal their identities or create multiple accounts. Our advanced Fuzzy Match algorithm catches these minor inconsistencies, typos, and even deliberate modifications with exceptional precision. This algorithm identifies data with a certain degree of similarity, even without an exact match, ensuring that fraudulent attempts are not overlooked. For example, details like writing “J. Smyth” instead of “John Smith” or using different capitalization in addresses are easily detected. This feature neutralizes such variations, one of the most common concealment tactics used by fraudsters.
Synthetic identities are typically created using entirely fabricated information or by combining details from different individuals. One of the most common methods for hiding these synthetic identities is the use of fraudulent addresses. Our Fake Address Detection engine effectively prevents this. The engine analyzes the authenticity and validity of addresses and determines if they have been used in fraudulent activities in the past. By integrating with geographic databases, postal code verifications, and known fraud patterns, it instantly identifies suspicious addresses. This allows us to uncover the complex networks and fraudulent identities established by fraudsters.
How is the Application Risk Score Calculated?
While traditional fraud detection methods only offer alerts, our platform provides a transparent risk score. This score not only indicates the fraud potential of an application or transaction but also clearly explains the underlying reasons for that likelihood. Our risk score is powered by comprehensive data analysis. This allows you to quantitatively measure the fraud risk and its causes (such as IP address, inconsistent information, or anomalous transaction patterns) and see clearly that the risk is based on concrete data.
With this comprehensive risk score, you can significantly optimize your operational processes:
Automated Approval/Rejection Decisions
Low-risk applications can be automatically approved by the system. This reduces the need for manual review and accelerates processes. Similarly, applications with a very high and obvious fraud risk are automatically rejected, preventing human resources from being tied up unnecessarily. This automation ensures confidence and efficiency in your decision-making processes.
Prioritization for Manual Review
High-risk applications and transactions are automatically prioritized for manual review. This allows human resources to focus on the areas requiring the most attention. Instead of reviewing every application from start to finish, analysts can focus on the potential risk points identified by the system, enabling them to make fast and accurate decisions. This prioritization increases operational efficiency and provides a proactive approach to fighting fraud.

Mastercard Ekata Module
Our Mastercard Ekata Module offers high security and precision in identity verification processes. With its advanced analytical capabilities and extensive database, it minimizes fraud risks and quickly and reliably verifies the information provided by users. It delivers identity verification and fraud risk scores using parameters such as name, surname, phone number, email address, IP address, and physical address. Additionally, it provides demographic information and geolocation analysis to create more comprehensive user profiles. In summary, it meets all address, email, and phone verification needs within a single solution. These features make it ideal for the gaming, e-commerce, and fintech sectors in combating application and account opening fraud.
Who Is It For?
Financial Institutions
Financial institutions and credit providers face significant financial and reputational risks from fraud methods like application fraud. These fraudulent activities, carried out using fake identities and falsified information to access credit and financial products, lead directly to financial losses and damage the institution's credibility.
E-commerce and Online Services
In the digital world, account opening fraud—such as promo hunting, coupon abuse, and return fraud—is a major problem for businesses, leading to revenue loss and reputational damage. Preventing this type of fraud helps build a genuine customer base, increases revenue and customer loyalty, improves marketing efficiency, protects brand reputation, and reduces operational costs. Application fraud detection and prevention systems are critical for businesses to prevent financial losses and achieve sustainable success.
Crypto Asset Service Providers
As the digital asset market grows, Crypto Asset Service Providers (CASPs) are battling threats of application fraud and fake accounts. An effective Application Fraud Solution proactively detects indicators of fraud, such as fake and synthetic identities and repeated access attempts, thereby preventing financial losses and reputational damage. Through automated risk assessment and AI analysis, fraud is prevented, costs are reduced, and regulatory compliance is ensured.
Fintechs
For fintechs, detecting fraud at the application stage is vital. Manipulated identities and "bust-out" schemes are common fraud methods. This method involves opening accounts with fake identities, maxing out credit limits, and then disappearing without repaying the debt.
Online Gaming Companies
Protect your business from bonus, campaign, and promotion abuse. In the digital world, organized fraud networks use automated bots to create multiple accounts, draining your marketing budget and disrupting a fair competitive environment. With our advanced solution, you can detect fake accounts and prevent campaign and bonus abuse using IP analysis, behavioral tracking, and artificial intelligence. Our machine learning-based solution learns new fraud tactics to prevent future abuse, keeping you one step ahead of your competitors. Enhance customer trust and satisfaction by offering a fair system. A trustworthy platform strengthens your user base and brand value.
Application Fraud Scenarios
Fraudsters typically target application processes for credit cards, bank loans, insurance policies, or other financial services. Each scenario presents a different approach and carries distinct risk profiles.
Synthetic Identity Fraud
Synthetic identity fraud is one of the most sophisticated types. Fraudsters create a "synthetic" identity by combining a piece of verifiable information, such as a real national ID number, with fake personal data. They use this identity to open low-limit accounts and build a positive credit history through regular payments. Once they secure a sufficient credit limit, they max out all available credit and disappear. Because there is no single real victim, this type of fraud is difficult to detect and causes significant losses for financial institutions.
Third-Party Fraud (Identity Theft)
This is the most well-known and widespread type of fraud. The fraudster illegally obtains another person's complete personal information. This can include their name, address, date of birth, Social Security/National ID Number, mother's maiden name, and even bank account details. The fraudster uses this stolen information to open new accounts, apply for loans, sign phone contracts, or attempt to access existing accounts in the victim's name, all without their knowledge. Detection of this type of fraud often occurs when the victim notices unexpected transactions on their bank statements or credit reports or receives notifications from debt collection agencies. Identity theft can have devastating financial and emotional consequences for its victims.
First-Party Fraud
The applicant uses their real identity but intentionally misrepresents their financial situation. The goal is to obtain credit approval, a higher limit, or more favorable payment terms. They might inflate their income, submit fraudulent documents, or conceal existing debts. For example, they might overstate their income by 50% or fail to declare debts with other banks. Often, the intention is never to repay the borrowed funds. They cause significant credit losses for institutions by applying to multiple lenders simultaneously and then disappearing without making payments.
'Bust-Out' Fraud
Fraudsters build trust by acting like exemplary customers with new credit cards or accounts. They make small purchases and pay them off regularly to build their credit score and secure higher limits. Once they reach a sufficient limit, they abruptly max out the credit line or take cash advances and then disappear without repaying the debt. These "bust-out" schemes are difficult to detect because no suspicious behavior is exhibited initially.
Digital Manipulation
This involves altering existing documents using advanced software (such as Adobe Photoshop or Illustrator). Income amounts on payslips, balance information on bank statements, address details on utility bills, or photos on identity documents can be modified. For instance, a salary of 5,000 USD can be changed to 15,000 USD, or a bank statement with a low balance can be altered to show a high balance.
Document Fabrication
In some cases, fraudsters create entirely fake documents from scratch. These can include counterfeit ID cards, passports, utility bills, payslips, or bank reference letters. These documents may be produced using professional printing techniques and security features similar to genuine ones, making them difficult to detect. The goal is to deceptively verify the applicant's income, address, identity, or employment status.
Fraud Malware Engelleme Hakkında Sıkça Sorulan sorular
Application Fraud is the act of fraudsters applying for financial products and services, such as loans, credit cards, or account openings, using fake, stolen, or manipulated identity, address, and income information. The objective is to obtain illicit gains and cause financial loss to institutions.
Our solution is ideal for many industries that face the risk of fraud in their application processes. Our primary target audience includes:
Financial Institutions and Banks: To prevent loan and credit card fraud.
E-commerce and Online Services: To prevent promotion and coupon abuse, fraudulent account openings, and return fraud.
Fintechs: To protect against modern fraud methods like “bust-out” and to secure their rapid growth processes.
Crypto Asset Service Providers: To prevent accounts opened with fake and synthetic identities and to stop illegal activities.
Online Gaming Companies: To block organized fraud networks and bot accounts that abuse bonuses and promotions.
Our platform increases efficiency by optimizing manual review processes:
Automation: Very low-risk applications are automatically approved, while obvious fraud attempts are automatically rejected.
Prioritization: It allows analysts to focus their time on the riskiest cases.
Speed: Real-time analysis ensures that the application processes for legitimate customers are not delayed.
Reduced Workload: The AI engine self-learns new fraud trends, reducing the burden on teams to constantly write new rules.
We have designed the integration process to be as simple as possible. Our solution can be easily connected to your systems via standard APIs. Depending on your technical team’s experience, the basic integration can typically be completed within a few days to a week. Our technical support team will guide you step-by-step throughout the process.
For the basic integration, a software developer who can work with APIs is sufficient. You do not need a team of data scientists to manage the platform. Our user-friendly interface and flexible rule engine allow your operational teams or analysts to easily manage the system.
It is definitely not a black box. Transparency is one of our top priorities. Our platform clearly explains the reasons behind the Risk Score generated for each application. For example, we provide concrete justifications such as, “IP address was previously used in fraud,” “There is an inconsistency in the entered information,” or “Behavioral patterns are suspicious.” This greatly simplifies the work of your manual review teams.
No, on the contrary, it has a positive impact. Since our system operates in real-time (within seconds), it does not cause any delays for legitimate customers. In fact, by automatically approving reliable applications with a low Risk Score, it speeds up the process and increases customer satisfaction. Our goal is not only to block fraudsters but also to clear the way for your good customers.
Thanks to the hybrid structure of our AI and rule engine, we aim to keep the false positive rate to a minimum. The system directly blocks obvious fraud while directing suspicious cases in the gray area to manual review. With customizable rules and risk thresholds, you can adjust the system’s sensitivity according to your risk appetite, minimizing the risk of blocking legitimate customers.
We will be sharing our customers’ personal data with you. How do you ensure data security and privacy?
Data security and privacy are our highest priorities. We are fully compliant with major international data protection regulations, such as GDPR, and are committed to adhering to local data privacy laws applicable to our clients. To support your compliance needs, we offer flexible data residency options, allowing your data to be stored in high-security, certified, and redundant data centers in your chosen region (e.g., EU, North America, etc.). All data is protected with industry-standard measures, including end-to-end encryption (both in transit and at rest), strict access controls, and regular security audits to ensure the highest level of protection.
Yes, our pricing model is flexible. The specified packages are a starting point. As your usage increases or decreases, we will contact you to create the most suitable and fair pricing model for your needs together. Our goal is to build a partnership that can scale with your business growth. You will not encounter any surprise costs.
Our 7/24 support is not just for emergencies and outages but also for your operational needs. You can also get assistance from our expert team on topics such as quickly creating a rule set against a new fraud trend, optimizing existing rules, or interpreting reports.
The integration is extremely simple.
For Websites: A single JavaScript snippet to be added to your site is sufficient.
For Mobile Apps: A lightweight SDK (Software Development Kit) is available to be added to your application.
Your technical team can complete this process within days.





















