Delivering true end-to-end fraud protection for Account Opening, login, Activity and Orchestration.
Use case > Digital customer onboarding
Improve the activation rates of genuine customers and prevent fraudsters from gaining access to your services.
Udentify Digital Onboarding
Menu
How it works
1. Scan ID
2. Take a Selfie
3. Result
Udentify offers a precise and speedy digital customer onboarding solution that guarantees customer satisfaction by successfully onboarding more users through a dependable and quick process, keeping the regulator’s content and reducing the cost of customer acquisition.
Features
How fraud.com helps.
Fast and accurate.
AI document verification, face matching and passive liveness detection provides precise onboarding results in around 15 seconds, giving a clear answer to either ‘yes’ or ‘no’.

Mostly everything.
Udentify verifies identity in 248 countries and territories over 12,000+ document types.
All devices GO
Complete the digital customer onboarding process on one device, or start on one device and end on another.
Automation.
OCR, NFC, no worries
Fraud.com’s autopilot precisely identifies customers’ ID documents to minimise errors.
Fraud.com’s autopilot precisely identifies customers’ ID documents to minimise errors.

Smart guidance.
Delivering low-friction identity verification. Our Intelligent ID SDKs guide the user with real-time blur, too close, too far, face not found, take off your mask, and too many faces boosting conversion rates by 15%.
Fraud prevention.
At Udentify, we utilise
cutting-edge AI fraud detection technologies to differentiate between trustworthy customers and fraudulent ones.
Protecting the customer, your brand and reputation.
cutting-edge AI fraud detection technologies to differentiate between trustworthy customers and fraudulent ones.
Protecting the customer, your brand and reputation.
Meet regulatory compliance mandates.
Proof of identity in seconds to meet your AML, KYC and KYB requirements.

Tailored for
your business.
Our Intelligent ID SDK is fully enabled to integrate with your onboarding process seamlessly.
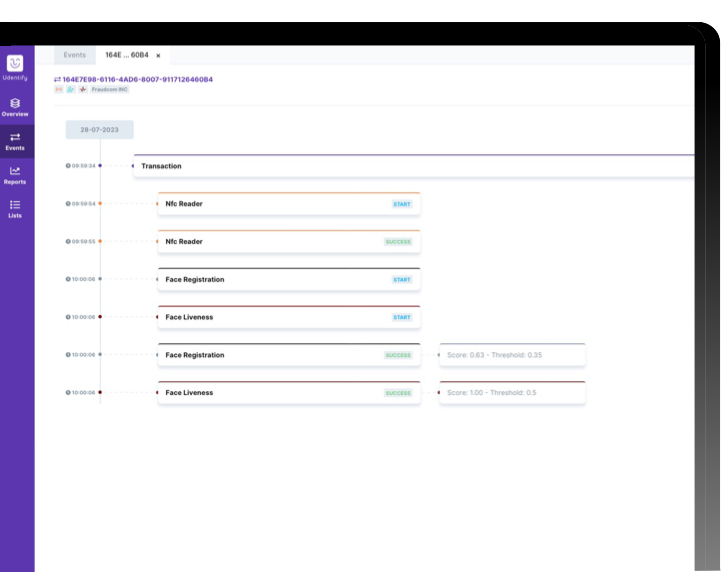
Gain a complete picture of your customers onboarding and biometric authentications with the Udentify identity hub.
Resources
Keep up to date with the latest onboarding insights.

This comprehensive article seeks to demystify digital onboarding, outlining its function and value across diverse industries.

Learn how to improve customer activation rates and keep the fraudsters out of abusing your services.
Case Study
FAQ
What is digital customer onboarding?
Digital customer onboarding refers to enrolling a new customer to a company or subscribing a new user to a service using their mobile device. The key objective of digital customer onboarding is to authenticate the identity of the enrolled person to ensure that they are who they claim to be.
To achieve this, facial biometrics and liveness detection technology, along with identity document processing, are employed to verify the user’s identity digitally and remotely.
To achieve this, facial biometrics and liveness detection technology, along with identity document processing, are employed to verify the user’s identity digitally and remotely.
What documents are supported ?
Passports, Driving licenses and government-issued ID cards. Udentify supports 12,000 document templates currently and we are constantly adding new templates as required.
What is passive liveness detection ?
An artificial intelligence-assisted verification method that detects whether the presented person is a live person and not a spoof (i.e. video, image or mask). Udentify passive liveness detection works in the background to speed up the onboarding, age verification and authentication process. It also; does not present the technology to fraudsters to leave doubt in their mind, as no fraudster likes to show their face.
Udentify passive liveness detection is iBeta ISO 30107-3 Level 1 & Level 2 certified, delivering the confidence that only your onboarded live customers can access your services.
Udentify passive liveness detection is iBeta ISO 30107-3 Level 1 & Level 2 certified, delivering the confidence that only your onboarded live customers can access your services.
How does Udentify verify the legitimacy of ID documents ?
To complete the digital customer onboarding process, the individual’s identity must be entered into the system.This can be done in two ways using NFC or OCR technologies.
NFC technology is used for documents that adhere to ICAO-9303 standards, such as chip ID cards, passports, and driver’s licenses.
OCR technology is used for non-chip documents like driver’s licenses or government-issued IDs.
NFC technology is a wireless communication system that enables data exchange between devices with one touch. Udentify’s NFC technology quickly reads identity information from chips and saves it to the Udentify server without additional documents.
OCR technology is an AI-based technology that processes text from scanned documents or image files.
Udentify uses OCR to quickly process and save identity information from chipless identity documents without additional data entry.
NFC technology is used for documents that adhere to ICAO-9303 standards, such as chip ID cards, passports, and driver’s licenses.
OCR technology is used for non-chip documents like driver’s licenses or government-issued IDs.
NFC technology is a wireless communication system that enables data exchange between devices with one touch. Udentify’s NFC technology quickly reads identity information from chips and saves it to the Udentify server without additional documents.
OCR technology is an AI-based technology that processes text from scanned documents or image files.
Udentify uses OCR to quickly process and save identity information from chipless identity documents without additional data entry.
What is digital onboarding in banking ?
Recently, biometric-based digital onboarding has gained significant popularity, particularly in banking, due to the pandemic. Digital or client onboarding in the banking sector refers to the process of signing up for banking services, including opening a bank account entirely online, usually through a mobile device.
Banks and other financial institutions are legally bound to know their customers and perform Know-Your-Customer (KYC) checks or procedures. When onboarding clients remotely, a secure and reliable way of verifying a client’s identity digitally is vital. This process is called eKYC or electronic Know Your Customer, as it is entirely digitised.
Within the eKYC process, banks or financial institutions must ensure that the client is genuinely who they claim to be. This can be challenging to verify remotely, primarily due to the rise of online identity fraud and deep fakes. That’s why fully remote digital onboarding steps in.
During the digital customer onboarding process, the client’s identity is verified by 1. validating their identity document and 2. matching their presented face using AI face verification to the validated identity document to check they are the right person, simultaneously checking that they are a real live person using passive liveness detection.
Banks and other financial institutions are legally bound to know their customers and perform Know-Your-Customer (KYC) checks or procedures. When onboarding clients remotely, a secure and reliable way of verifying a client’s identity digitally is vital. This process is called eKYC or electronic Know Your Customer, as it is entirely digitised.
Within the eKYC process, banks or financial institutions must ensure that the client is genuinely who they claim to be. This can be challenging to verify remotely, primarily due to the rise of online identity fraud and deep fakes. That’s why fully remote digital onboarding steps in.
During the digital customer onboarding process, the client’s identity is verified by 1. validating their identity document and 2. matching their presented face using AI face verification to the validated identity document to check they are the right person, simultaneously checking that they are a real live person using passive liveness detection.
What is next for liveness detection ?
There are two types of liveness today, passive and active. Passive liveness does not require any action from the user, while active liveness does. Active liveness may be more beneficial for frequent logins but can also cause friction and lead to high abandonment rates for new customers. It is essential to consider the differences between the two approaches when deciding which one to use.
← Swipe left to view the content of the table
| Active | Passive | Hybrid | |
| User experience | Users are required to respond to “challenges” (i.e. look left, look right etc) that may increase the time and effort needed for the process. | This process does not require any action from the user, which reduces any difficulties and decreases the likelihood of users abandoning the process, especially in cases of remote digital customer onboarding. | Hybrid liveness detection is a new form combining active and passive liveness detection. However, unlike the typical active detection on its one, when combined with passive liveness detection, any customer actions (challenges) are coupled, thus validating the presented user is the right person. |
| Image Analysis | Requires analysis of multiple images or frames of video to detect movement. | The analysis can be carried out using a single image and processed almost instantly. | |
| Speed | Active liveness always increases user effort, resulting in a more extended liveness check. | Near real-time. | |
| Bandwidth requirements | It may be necessary to exchange more data between the user’s device and a server-based solution. | Passive liveness detection uses the same selfie used for facial recognition, resulting in no incremental traffic to the server. | |
| Robustness of spoofing | Fraudsters can use active systems to figure out how to bypass the liveness check. They can easily reverse-engineer the instructions provided to them. Some standard methods they use to break through include using a 2D mask with holes for the eyes or animation software to imitate head movements, smiling, and blinking. | There is an advantage to using passive methods for security, which is known as “security through obscurity.” These methods are less susceptible to spoofing attacks, as the perpetrator does not have any clues as to how to bypass the liveness check. In fact, they may not even be aware that the check is taking place. |

Ready for the new era of identity, authentication and fraud prevention?
Our experts are here to answer your questions and help you with every step to make sure fraud.com solutions are suitable for your needs.
Complete the form on the right, and we will contact you back as soon as possible.
Get in touch

























