Bringing order to the chaos of fraud prevention operations
fcase unified risk operations combines your defences to help you better manage fraud prevention more effectively and efficiently.
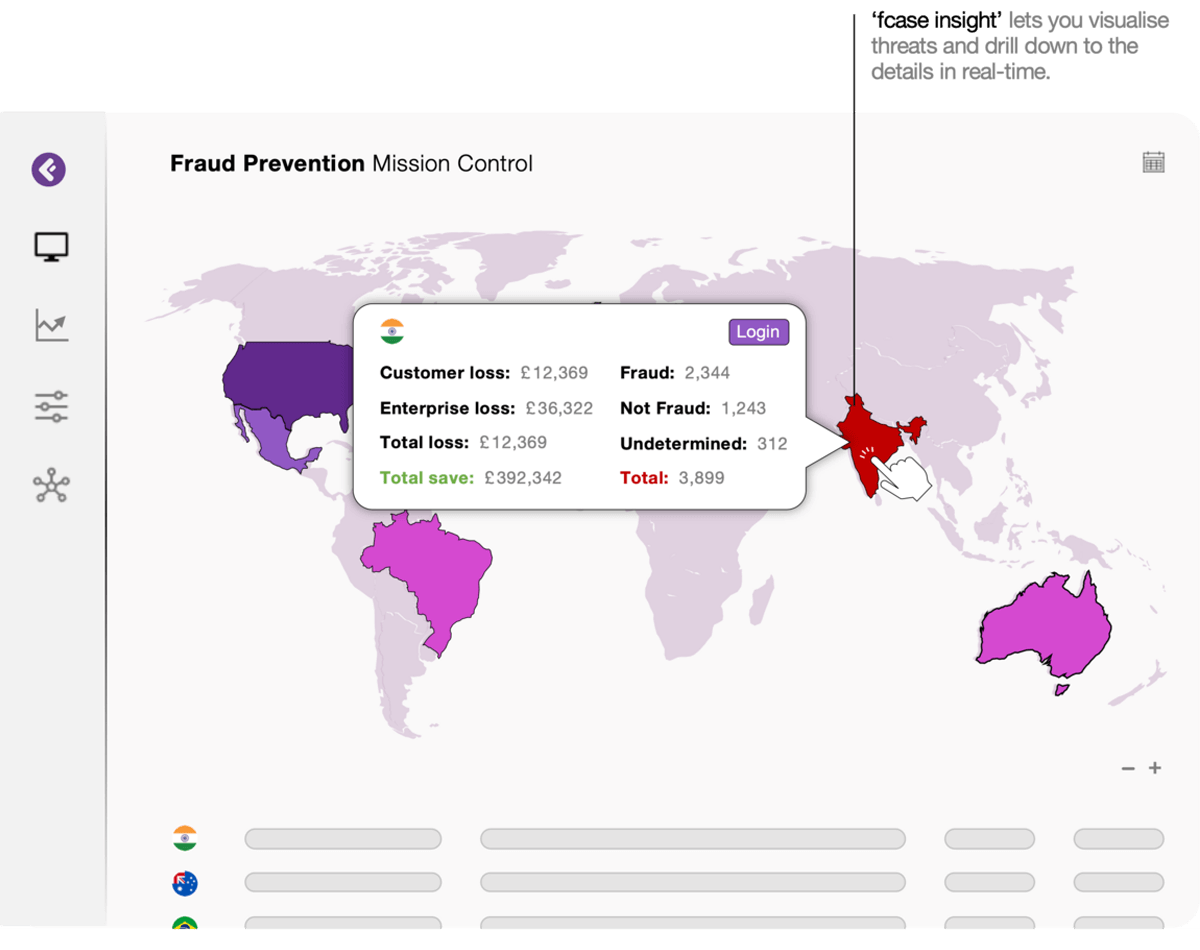
See the big picture of fraud.
Meet a single attack with a united defence.
Less friction, less fraud, less inefficiencies.
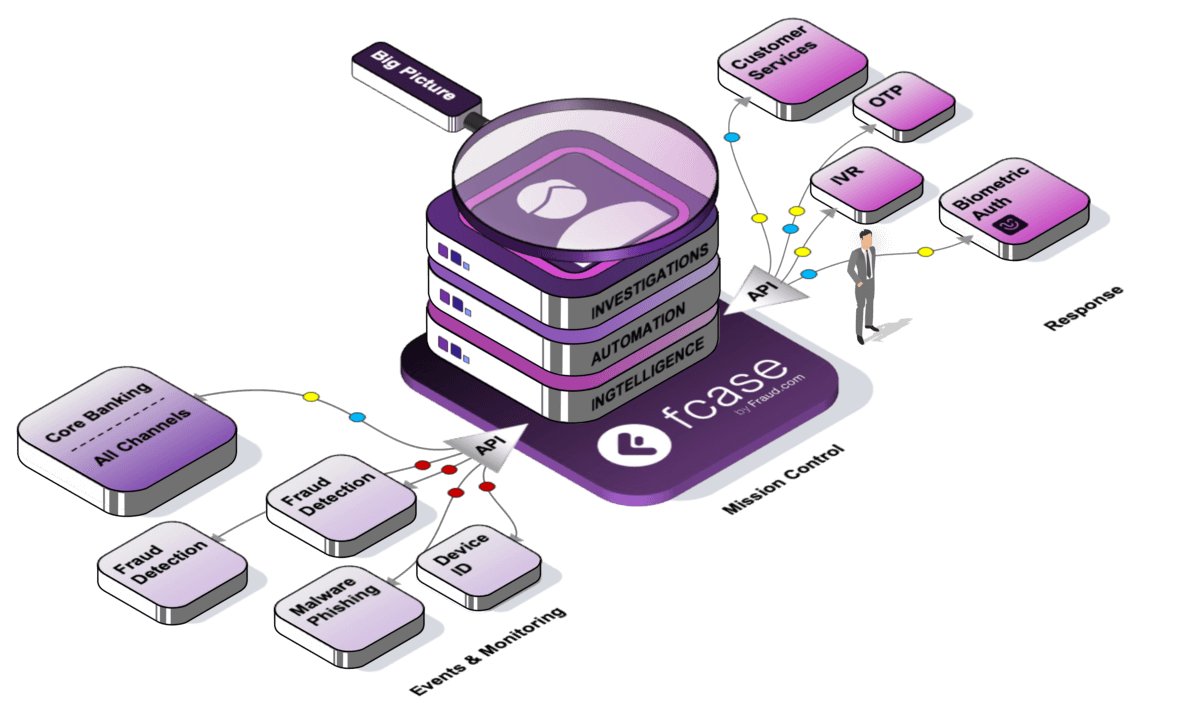
One mission control, three distinct layers.
A holistic view of fraud prevention.
Bringing your data to life.
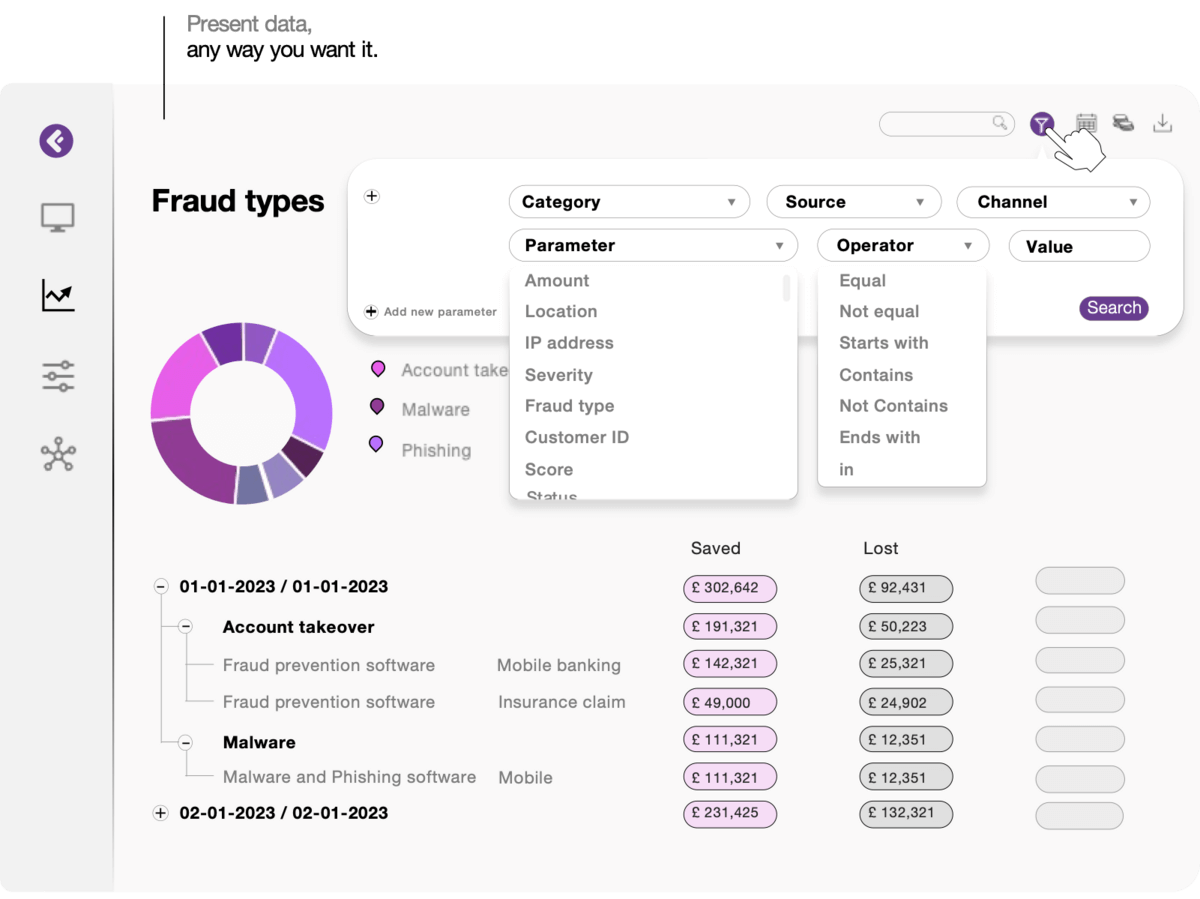
Comply with confidence
Evoluate performance
Comply with confidence


Evoluate performance
Automate to reduce risk.
Improve customer experiences.
Streamline tasks.
One platform, endless automation
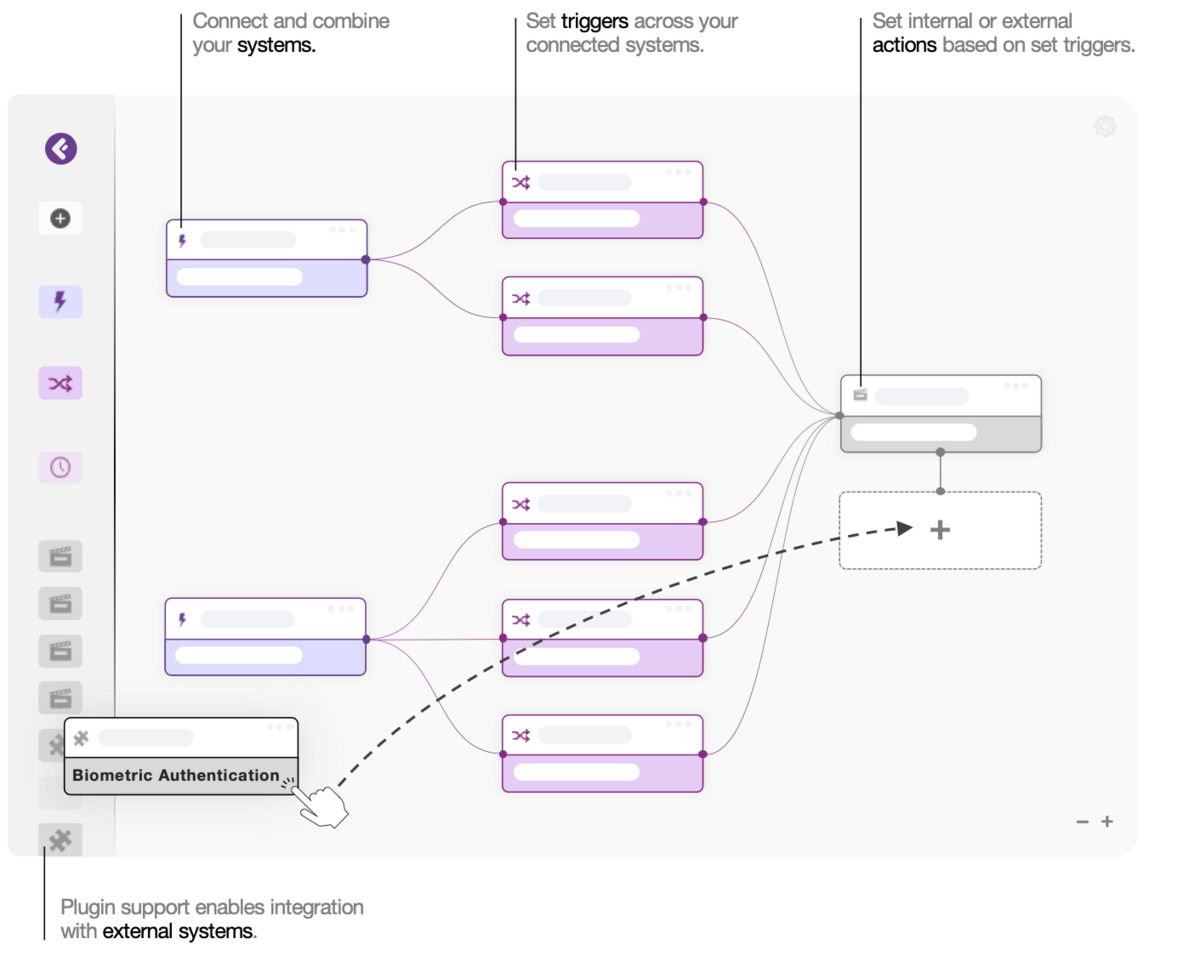
Automate to deliver a unified fraud response.
Automate to improve efficacy and efficiency.
Free your operational resources up from repetitive tasks to reduce costs, increase productivity, improve visibility and reduce errors.
What will you automate?
Unified case management.
Designed to make
a difference
Connecting the dots.
Ready to respond to threats more effectively and efficiently?
Benefits

Single source of truth.

Uplifting user experiences.

Boosting productivity.
Contact us for more examples →

Reducing risk.

Reducing costs.

Intelligence all around.
Resources
Case Study
Challenge
Results
FAQ
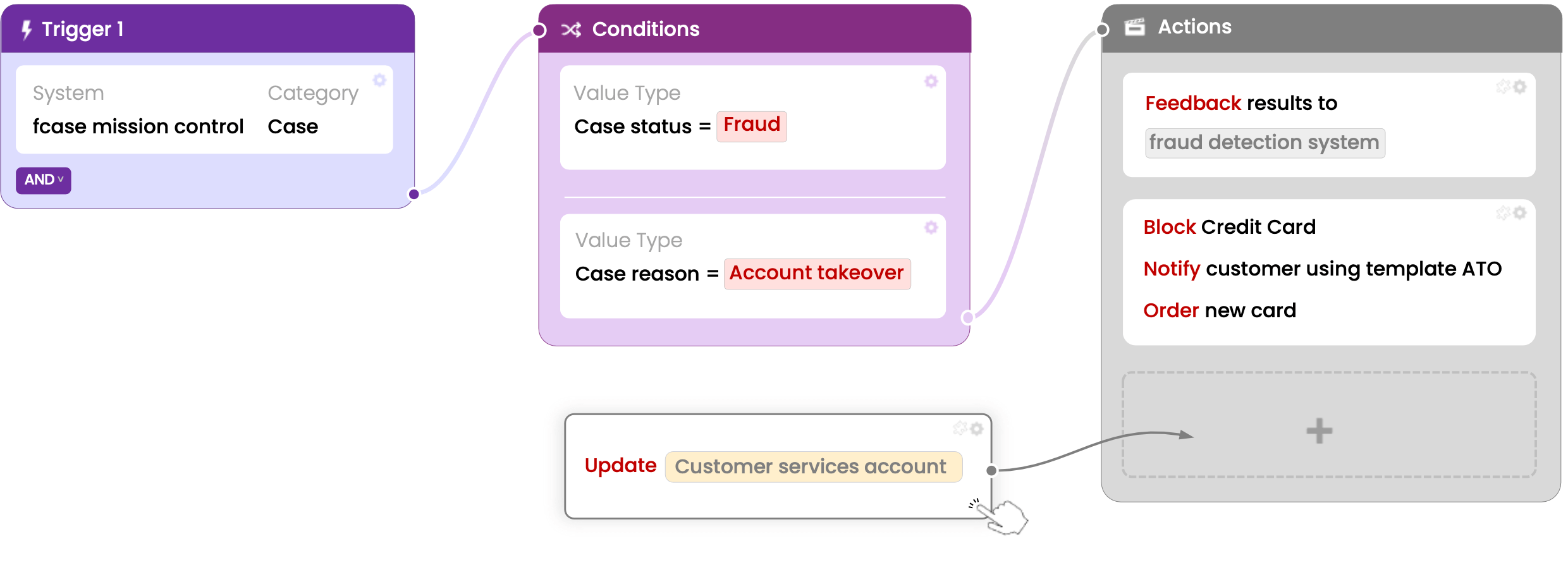
fcase Unified Risk Operations (AKA fraud orchestration) integrates operational, anti-fraud, identity, and cyber tools to create a central mission control that provides a single source of truth. This helps improve the customer experience while reducing fraud and operating costs.
As an organization grows, its fraud prevention measures can become more complicated to sustain. With the introduction of new business channels, outdated systems that need replacing, and the need to fine-tune modern systems, managing fraud prevention can become overwhelming. This issue is compounded when the organization operates across multiple countries and involves numerous people, leading to a disjointed approach that can be chaotic.
By breaking down siloes, a fraud mission control unites your defences and provides a single source of truth. This results in a highly efficient fraud foundation that reduces fraud loss and improves both customer experiences and the day-to-day activities of fraud professionals.
fcase fraud mission control has three modules: Intelligence, Automation, and Investigations.
– Intelligence offers a big-picture overview of fraud across the entire fraud stack.
– Automation assesses user risk and streamlines operations.
– Investigations centralise case management to reduce fraud loss and speed.
fcase fraud mission control glues systems together so they can sing in harmony. The systems being glued, in reality, are varied and full of specific integration points and data sets.
At fraud.com, we understand that every customer is different; our team has decades of experience uniting systems to form a central view, and we built fcase fraud mission control for this job. We have a myriad of connectors and APIs for your various defences, ranging from JSON, XML, TCP/IP Socket, DB, CSV and Kafka; furthermore, flexible data tools to map, label and mask so you can get your data just as you want it.
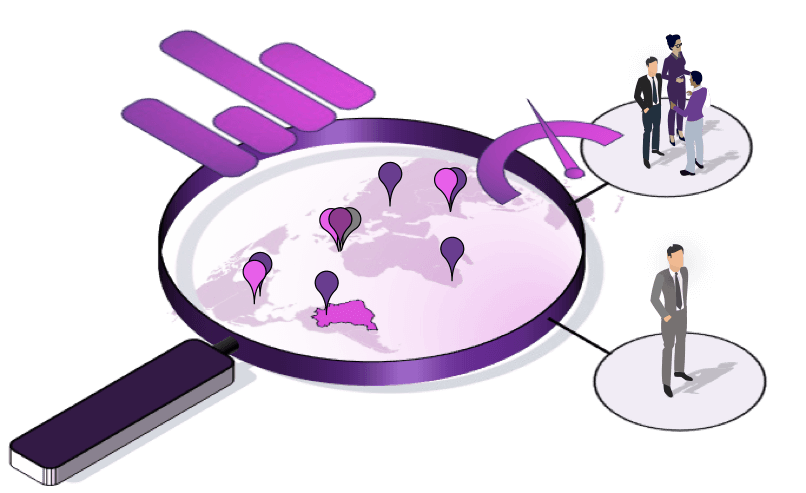
A threat-centric approach consolidates all alerts and their related data to provide a complete context or story; this enables a single investigator to conduct a faster and more accurate assessment than multiple investigators.
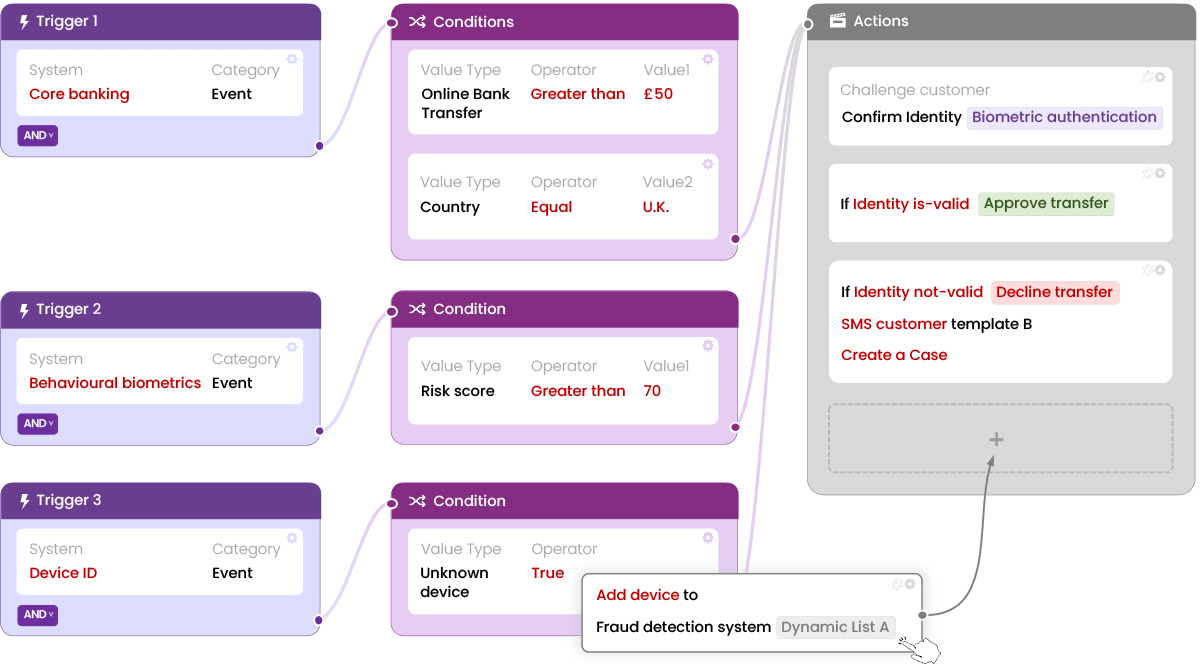
Here is just one example of a typical attack:
A fraudster (Jack) takes over (Jason’s) bank account (ATO). Firstly Jack sends Jason an email (Phishing). Jason clicks a link in the email (and ends up with malware); this malware captures his keystrokes on his device and sends them to Jack, which contains some personal information and login credentials. Jack then logs into Jason’s bank account; during login, the bank defences detected a new device and behavioural change, so when Jack made an external money transfer, the bank sent a one-time password to confirm it was Jason; nevertheless, Jack already had compromised Jason’s phone number, and Jack receives the one-time password so he can carry on with the transaction / fraud.
In the example above, the typical alert-centric approach evaluates fraud cases individually, missing any relationships between them, leading to higher fraud loss, more extended investigations, wrong decisions made, higher investigation costs and more customer friction.
In the threat-centric approach, the example above would be one threat and, therefore, one case with the full context. The net result is that the customers are better protected, and less money is lost and spent.
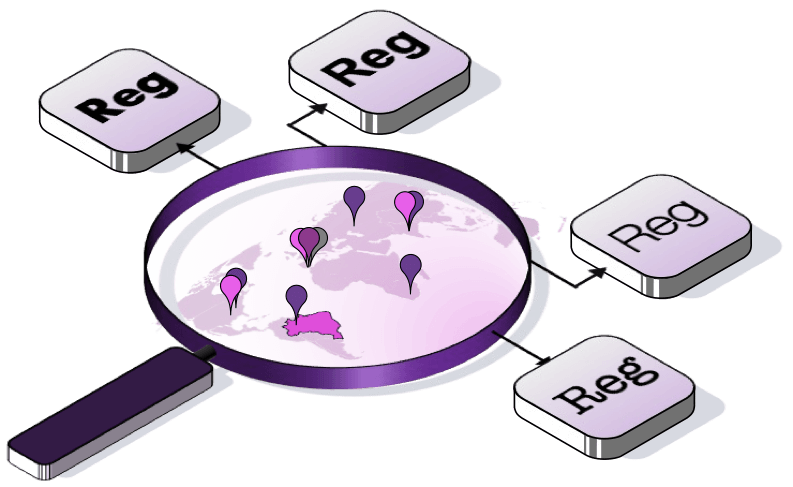
Financial institutions are required by law to file a Suspicious Activity Report (SAR) or Suspicious Transaction Report (STR) when they detect any suspicious or potentially suspicious activity related to money laundering, financing of terrorism, or other financial crimes. The criteria for reporting vary from one country to another but generally include any financial transaction that is either:
- Does not make sense to the financial institution.
- Unusual for that particular client.
- Designed to conceal or obscure another transaction.
These reports are submitted to the financial crime enforcement agency of the respective country, which is responsible for collecting and analyzing transactions and reporting them to relevant law enforcement teams.
To prevent money laundering, banks use a form called a currency transaction report (CTR). A bank representative must complete this form whenever a bank customer attempts a currency transaction above a certain amount. This is part of the banking industry’s responsibility to combat money laundering. To prevent financial crimes, CTRs require institutions to verify the identity and Social Security numbers of anyone attempting a significant transaction, regardless of whether they have an account with the institution.
Payment service providers must provide statistical data on payment fraud to regulatory authorities annually.
Ready for the new era of identity, authentication and fraud prevention?
Our experts are here to answer your questions and help you with every step to make sure fraud.com solutions are suitable for your needs.
Complete the form on the right, and we will contact you back as soon as possible.