Cloud KYC / KYB
KYC stands for “Know Your Customer,” a process used to verify customer identities, commonly employed in the financial sector. In remote identification, customers submit documents such as passports or ID cards, which are then automatically verified.
These processes are rigorously monitored by regulatory bodies worldwide, including the Securities and Exchange Commission (SEC) and Financial Crimes Enforcement Network (FinCEN) in the U.S., the Financial Conduct Authority (FCA) and Prudential Regulation Authority (PRA) in the UK, and the European Securities and Markets Authority (ESMA) and national Financial Intelligence Units (FIUs) across Europe. Globally, the Financial Action Task Force (FATF) sets anti-money laundering (AML) and counter-terrorism financing (CTF) standards, ensuring alignment with frameworks like the EU’s GDPR and the U.S. Bank Secrecy Act. By adhering to these regulations, KYC safeguards both businesses and customers while ensuring compliance with local and international legislation.
Affordable Advanced Cloud KYC / KYB Solution
Discover our cost-effective Cloud KYC packages, designed with cutting-edge features for seamless remote identity verification. Fully compliant with global regulations, including GDPR, FATF, and eIDAS.
*Fees are charged monthly in advance. Prices exclude VAT.
Technical Specifications
|
Our high-accuracy facial recognition technology is certified by the U.S. National Institute of Standards and Technology (NIST). This certification ensures reliable and precise identity authentication processes, minimizing fraud. NIST Certified Facial Recognition
To review the NIST test results Click Here |
This algorithm ensures the user is a real person by prompting them to perform specific actions, such as turning their head, blinking, or smiling. This helps prevent fraudulent identity attempts, such as using photos or videos to impersonate someone. Active Face Liveness Detection
|
||
|
This algorithm verifies the presence of a live person by analysing camera image data, such as depth perception and skin texture, without requiring any special actions from the user. It enhances security by reducing the risk of spoofing while providing a seamless user experience. Passive Face Liveness Detection
|
Hybrid liveness detection combines advanced biometric verification technology by simultaneously integrating both active and passive methods for enhanced security and accuracy. Hybrid Face Liveness Detection
|
||
|
The ISO 30107-3 Level 1 liveness detection certification is a biometric algorithm standard designed to identify basic fraud presentation attacks. This Level 1 category focuses on preventing low-skill attacks, such as two-dimensional photocopying or on-screen image and video presentations. It effectively detects these fakes using basic vitality indicators, such as movement or light changes. ISO 30107-3 Level-1 Liveness Detection
Click here to review our ISO 30107-3 Level-1 Liveness Detection Certificate. |
The ISO 30107-3 Level 2 liveness detection certification validates biometric algorithms that can detect more advanced presentation attacks. This Level 2 standard identifies sophisticated spoofing methods, such as 3D masks or high-resolution deepfakes. These algorithms effectively prevent spoofing by using advanced liveness indicators, including facial tissue analysis and depth detection, to monitor subtle changes in movement or lighting conditions. ISO 30107-3 Level-2 Liveness Detection
Click here to review our ISO 30107-3 Level-1 Liveness Detection Certificate. |
||
|
Leveraging advanced Near Field Communication (NFC) chip reading technology, we can swiftly and securely scan chips embedded in IDs and passports. This enhances data entry efficiency and significantly reduces the risk of manual errors. NFC ID / Passport Scanning
|
Our advanced Optical Character Recognition (OCR) technology automatically extracts text data from IDs, driver's licenses, and passports. This streamlines the data collection process, enhancing efficiency and significantly saving time. OCR ID / Driver's License / Passport Scan
|
||
|
The Energy Monitoring Module is designed to make identity verification processes more reliable and uninterrupted. This module monitors the device's charge status and power saving mode during eKYC processes, ensuring the seamless completion of verification procedures. For detailed information, Click Here ⇣ Energy Monitoring
|
The List Management feature offers organizations various list categories to securely and effectively manage identity verification processes. Organizations can create lists according to their needs with customizable list management, thereby managing customer segments more effectively and maximizing corporate reliability and user experience with security measures appropriate for each segment. For detailed information, Click Here ⇣ List Management
|
||
|
Helps prevent forgery by detecting the complex, repeating patterns (guilloche) found in the background of the document. The presence of these patterns is an important factor in verifying the document's authenticity. OCR Guilloche Detection
|
Detects the rainbow printing technique (printing with color gradients) used on the document. This special printing technique enhances document security as it is difficult to imitate and helps prevent counterfeiting attempts. OCR Rainbow Print Detection
|
||
|
Detects special optical inks used on the document whose color changes depending on light or viewing angle (Optically Variable Ink). This helps prevent unauthorized copying and fraudulent activities. OCR Optical Ink Detection
|
Detects latent images placed on the document that are normally invisible but can be revealed through special methods. This feature enhances document security and creates an additional layer against forgery. OCR Latent Image Detection
|
||
|
Verifies the document's authenticity by analyzing the presence and characteristics of holograms on the document. Holograms are security features that are difficult to replicate. OCR Hologram Detection
|
Detects extremely small text (microtext) on the document that is difficult to discern with the naked eye. This feature indicates that the document was produced according to high security standards and makes counterfeiting attempts more difficult. OCR Microtext Detection
|
||
|
Thanks to OAuth and OpenID support. Users you authorize can securely and quickly log in to the KYC Platform using their corporate credentials. This allows you to manage access and authorization policies for the KYC Platform. OAUTH / OpenID Support
|
We offer Android and iOS software development kits (SDKs) that you can easily integrate into your mobile applications. This enables you to implement mobile KYC processes seamlessly. iOS, Android, React, Flutter and WEB SDK
|
||
|
We offer a tool to help users easily locate the NFC chip on their ID cards or passports. This makes the scanning process more user-friendly. NFC Antenna Locator
Click Here ⇣ |
We provide a separate environment where you can safely test your integrations and features without affecting the live environment. This ensures the stability of your system. Test Environment
|
||
|
We provide a separate environment where you can safely test your integrations and features without affecting the live environment. This ensures the stability of your system. Production Environment
|
The Geolocation feature guarantees secure and seamless execution of eKYC processes. It provides crucial advantages in key business areas such as identity verification through IP addresses and location data, fraud prevention, enhanced security, personalization, and ensuring regulatory compliance. Geolocation
Click for more details ⇣ |
||
|
Our live support team is available 24/7 to answer your questions and resolve any potential issues. 24/7 Live Support
|
We provide free migration support to facilitate your transition process from your existing systems to our KYC product. Free Migration
|

What is Video KYC?
Video KYC, or remote identity verification via video call, is used when identity data cannot be fully read, the identification process is disabled, network connection issues occur, poor image quality makes recognition difficult, verification cannot be performed due to old or worn identity documents, or the user struggles to complete multi-factor authentication.
During the Video KYC process, the customer connects with a bank representative via video conference. Identity documents are displayed live, and biometric data is verified using facial recognition technology. To enhance security of the authentication process, physical security features on the ID, such as holograms, guilloche patterns, and special inks, are carefully checked. These elements play a critical role in preventing fraud and verifying the authenticity of the identity. This approach supports compliance with global and regional KYC standards, ensuring the prevention of fraud and money laundering.
What is Video KYC / KYB Operator Service?
The Video KYC Operator Service is ideal for businesses that lack sufficient in-house resources for identity verification. This service is available 24/7 and is operated by specially trained KYC experts who adhere to all relevant legislation and regulations. If needed, customers participate in the identity verification process via video conference with a Video KYC operator. During the session, identity documents are examined live in accordance with legal requirements, and accuracy is ensured through biometric data and facial recognition technologies. In addition, physical security features such as holograms, guilloche patterns, and special inks are scrutinized in detail. Careful examination of these elements is crucial for preventing fraud and verifying the authenticity of identities. All records related to the Video KYC service are securely stored in encrypted disk space.
How Does Self Service KYC Work?
Remote identification is conducted in accordance with regulations established by relevant supervisory authorities, particularly in sectors such as finance and other regulated industries. This process typically involves the following steps:
1.Application: The customer initiates the remote authentication process through the service provider’s website or mobile application.
2.ID Document Capture: The customer presents their ID card or passport for identity verification. The document’s information is automatically extracted using NFC (Near Field Communication) or OCR (Optical Character Recognition) technology. Algorithms analyse the extracted data for accuracy. If an issue arises in the self-service process, the authentication is completed via video call with a customer representative. The document reading system should be capable of processing both domestic and international passports.
3.ID Document Verification: The verification process varies depending on the method used. With NFC-based verification, the customer taps their NFC-enabled ID card or passport on an NFC-compatible smartphone, allowing secure data transfer. The biometric and identity data stored on the chip are authenticated using digital signature verification, ensuring that the issuing authority has digitally signed the information, preventing counterfeiting. In OCR-based verification, the identity document is scanned using the phone’s camera. OCR technology extracts and digitizes the text and images, while algorithms analyze security features such as guilloche patterns, rainbow printing, optical variable ink, hidden images, holograms, and micro-lettering. Additionally, facial photos and signatures on the document are checked for accuracy.
4.Biometric Verification: If the document was scanned via OCR, the verification is done using the printed photo, whereas NFC-based verification relies on the digital photo stored in the chip. Facial recognition algorithms must meet NIST (National Institute of Standards and Technology) standards to ensure high accuracy and compliance with international security guidelines. Key performance metrics include the False Match Rate (FMR), which measures the probability of incorrectly matching different identities, and the False Non-Match Rate (FNMR), which indicates the likelihood of failing to match a valid identity. NIST certification guarantees that the biometric verification process is secure, accurate, and resistant to fraud while optimizing the user experience.
5.Liveness Detection: To enhance security and regulatory compliance, both passive and active liveness detection methods are used. Passive liveness detection analyses natural facial characteristics such as size and lighting, while active liveness detection requires the user to perform specific movements to confirm their presence. To ensure fraud resistance, liveness detection algorithms must be certified under ISO/IEC 30107-3 Level 1 and Level 2, verifying their ability to detect spoofing attempts involving fake photos, masks, or other fraudulent techniques.
6.Final Review and Confirmation: Once all verification steps are successfully completed, the customer’s identity is confirmed, and the process is finalized. The service provider then sends a confirmation notification to the customer.
What is KYB?
KYB (Know Your Business) is a mandatory process for financial institutions, fintech companies, and other regulated businesses to securely verify the identity of legal entities (corporations, LLCs, etc.).
As the corporate equivalent of Know Your Customer (KYC) for individuals, KYB is essential for preventing money laundering and terrorist financing, ensuring transparency, and establishing secure business relationships. Regulatory frameworks established by bodies like the Financial Crimes Enforcement Network (FinCEN) in the US, the Financial Conduct Authority (FCA) in the UK, and international standards set by the Financial Action Task Force (FATF) necessitate robust KYB procedures. Compliance with data privacy regulations such as the GDPR (in Europe and influencing global standards) and relevant US state laws (like CCPA/CPRA) is also crucial throughout the process.
Recent regulatory updates often emphasize the need for reliable remote KYB (Corporate Identity Verification) processes, outlining detailed requirements for digital verification.
How the KYB Process Works
The KYB (Know Your Business) process is designed to efficiently and securely verify the identity of legal entities. Using Cloud KYC, this process is streamlined and ensures compliance with relevant regulations. Here’s how the typical KYB process flow works:
1. Application Initiation and Information Gathering
The KYB process begins with the collection of the legal entity’s essential information. An electronic application form captures key details like the registered business name, registration number (e.g., EIN in the US, Company Number in the UK), tax identification number, nature of business, and registered office address. This initial data is then cross-referenced with official sources such as Companies House (UK), Secretary of State databases (US), or other applicable commercial registers for preliminary verification.
Simultaneously, information about the individual(s) authorized to act on behalf of the entity is collected. This typically includes their full name, date of birth, a verifiable government-issued ID number, email, and phone number. This step lays the groundwork for subsequent identity and authorization verification stages.
2. Document Submission and Declarations
Next, the authorized representative(s) submit the required documentation and formal declarations. This includes a digitally captured statement confirming they are authorized to act for the company. Supporting documents are also uploaded, such as the company’s certificate of incorporation/registration, articles of association/bylaws, proof of address, and evidence of signatory authority (e.g., board resolution, power of attorney). This digital submission allows for efficient verification of the company’s status and the representative’s authority.
3. Data Verification and Cross-Checks
This crucial stage involves automated verification of the submitted information and documents against official public and commercial databases. Core company details are checked for accuracy and currency using data from government business registries, commercial databases, and tax authorities (like the IRS or HMRC). Simultaneously, the authorized representative’s details and their authority to act are verified against official records, confirming their identity and the scope of their representation powers.
4. Representative Identity Verification (Video KYC)
A key security measure involves remotely verifying the identity of the authorized representative(s) in real-time. A live video session is conducted via our secure platform. During the session, the representative presents a recognized government-issued photo ID (e.g., passport, driver’s license). Advanced biometric facial recognition, liveness detection, and document authenticity checks are performed automatically, potentially integrating with official verification services where permissible. If multiple representatives require verification, separate sessions can be efficiently managed.
5. Ultimate Beneficial Ownership (UBO) Identification
Regulatory requirements (like the Corporate Transparency Act in the US) mandate the identification of the Ultimate Beneficial Owners (UBOs) – the natural persons who ultimately own or control the entity. Information such as name, date of birth, address, and ownership/control details for individuals meeting the defined threshold (e.g., 25% ownership or significant control) is collected and securely recorded to ensure transparency.
6. Final Review, Approval, and Record Keeping
In the final step, all verified information, document checks, representative verifications, and UBO details are reviewed for completeness and compliance. Once everything is confirmed, the KYB process is successfully concluded, and the system formally approves the establishment of the business relationship. All data, verification steps, and outcomes are securely logged, creating a comprehensive audit trail for regulatory compliance (FinCEN, FCA, FATF standards) and internal governance. The applicant is notified of the successful completion, allowing the business relationship or service activation to proceed promptly.
What Are Anti-Money Laundering (AML) Checks?
Anti-Money Laundering (AML) checks are a critical component of the broader Know Your Customer (KYC) and Customer Due Diligence (CDD) framework mandated by global and local regulations (such as those set by FATF, FinCEN, FCA, ESMA, and national FIUs). While KYC focuses on verifying a customer’s identity, AML checks go a step further by assessing the potential risk associated with that customer, specifically concerning involvement in money laundering, terrorist financing, or other financial crimes. This involves screening customer data against various watchlists and databases to identify potential risks that require further investigation or specific actions.
How Do AML Checks Work within Cloud KYC?
- Sanctions Screening: Checking customer names and details against official sanctions lists issued by governments and international bodies (e.g., OFAC, UN, EU, HMT). This helps prevent dealings with individuals or entities under economic sanctions.
- Politically Exposed Persons (PEP) Screening: Identifying individuals who hold prominent public functions (PEPs), as well as their relatives and close associates (RCAs). Transactions involving PEPs often require enhanced due diligence due to a higher potential risk of corruption or bribery.
- Adverse Media Checks (Optional/Future Enhancement): Scanning reputable news sources and databases for negative information linked to the customer, which might indicate involvement in financial crime or other relevant risks.
- Risk Assessment: Based on the screening results, the system can help assign a risk score or flag potential matches, enabling businesses to apply appropriate levels of due diligence according to their risk-based approach.
- Integrated Workflow: AML checks are designed to integrate seamlessly into the overall customer onboarding and monitoring process offered by Cloud KYC, providing a unified view of customer identity and risk.
- Compliance and Audit Trail: All checks and their results are logged securely, providing a clear audit trail for regulatory reporting and internal compliance reviews.
Mobile KYC / KYB App
The Mobile KYC / KYB App, offered as part of our Cloud KYC service, is a powerful solution for remote identity verification that ensures full compliance with legal regulations. Powered with NFC and OCR-based ID capturing technologies, the app enables fast and reliable verification of customer identity documents. Additionally, with Video KYC and Video KYC Operator Service, users can complete identity verification via secure video conferencing. With our Mobile KYC application, there is no need to develop a separate solution for remote identification.
Mobile KYC is fully compatible with iOS and Android, the app can be easily downloaded from the App Store and Google Play. Our expert team manages all maintenance and updates to ensure seamless functionality. Security is a top priority, with multiple protective layers in place. To mitigate reverse engineering risks, the app includes data obfuscation, encryption, and anti-tampering measures. Advanced security protocols such as SSL pinning and device fingerprinting safeguard against man-in-the-middle attacks, ensuring robust protection. With these advanced security features, the Mobile KYC app delivers a fast, reliable, and legally compliant identity verification experience for your customers.
Geo-location
The Geolocation feature in Cloud KYC enhances the security and efficiency of eKYC processes by leveraging IP addresses and location data for identity verification. This advanced feature plays a crucial role in fraud prevention, security enhancement, user personalization, and regulatory compliance. By analysing users' geolocation data, businesses can detect suspicious activities, minimize security risks, and ensure transactions originate from authorized regions. This not only strengthens authentication accuracy but also improves the user experience by enabling seamless and secure identity verification. With precise location-based controls, businesses gain a powerful tool for fraud prevention and secure service delivery.
Back to the Table ⇡
S3 Storage
The S3 Storage support provided within our Cloud KYC service includes the S3 protocol, offering scalable and reliable data storage solutions. This advanced protocol enables users to securely transfer data to their own storage systems while enhancing speed and reliability. By integrating with existing infrastructure, organizations can maintain maximum data security and manage storage in compliance with their policies. With S3 support, data is stored in a flexible and accessible environment, allowing Cloud KYC users to optimize their processes with greater customization and control.
Back to the Table ⇡
Biometric List Management
The Biometric List Management feature in Cloud KYC enables organizations to manage identity verification processes securely and efficiently through various list categories. The blacklist flags suspected fraudulent users, ensuring their transactions are monitored or blocked. The greylist tracks users with unusual behavior who are not blacklisted, applying closer monitoring and additional verification when necessary. The VIP list enhances customer satisfaction by granting special privileges and priority service to high-value customers. The whitelist includes fully trusted users, allowing them to experience faster and more efficient transactions. Additionally, organizations can customize lists to meet specific needs, optimizing customer segmentation and enhancing security, reliability, and user experience.
Back to the Table ⇡
NFC Antenna Locator
The NFC Antenna Locator feature is designed to enhance the user experience by providing precise NFC antenna location data for thousands of devices stored in a comprehensive database. During the eKYC process, the NFC Locator accurately identifies the NFC antenna’s position on a user's device and shares this information in real-time. This enables users to quickly locate their NFC antenna and complete NFC ID scanning with greater ease and efficiency. By streamlining the verification process, the NFC Locator ensures a smoother user experience, reduces friction, and ultimately boosts conversion rates.
Back to the Table ⇡
Energy Monitoring
The Energy Monitoring Module enhances the reliability and continuity of authentication processes by tracking a device’s battery status and power-saving mode during eKYC transactions. By ensuring that verification processes are not disrupted due to low power, this module helps determine whether the necessary conditions are met before video calls and proactively detects potential interruptions. This approach significantly optimizes the user experience while preventing businesses from facing disruptions caused by device-related issues. The Energy Monitoring Module ensures a seamless and efficient eKYC process, improving both operational reliability and transaction success rates.
Back to the Table ⇡
Facial Recognition Algorithm Performance Analysis
The effectiveness of facial recognition algorithms is assessed based on key performance metrics. The Face Recognition Vendor Test (FRVT) conducted by the National Institute of Standards and Technology (NIST) serves as the internationally recognized benchmark for evaluating accuracy, speed, and overall performance.
Only algorithms that meet NIST performance standards should be used, making it essential for facial recognition providers to be listed in the NIST FRVT database. These criteria are crucial for ensuring the reliability, security, and accuracy of facial recognition technology.
A key benchmark in NIST testing is “FNMR @ FMR = 10⁻⁶”, which measures the system’s accuracy. This means that while the False Match Rate (FMR) is limited to 1 in a million, the False Non-Match Rate (FNMR) must remain below 1%, ensuring a high level of precision and trustworthiness in identity verification.
FNMR
(False Non-Match Rate)
FNMR refers to the rate at which two facial images, which should match, are incorrectly identified as different. In other words, it measures the probability that the system mistakenly classifies the same person as someone else. A low FNMR indicates that the facial recognition algorithm is accurate, reliable, and consistent in identifying individuals correctly.
FMR
(False Match Rate)
FMR, on the other hand, refers to the rate at which facial images of two different people are mistakenly identified as the same individual. A low FMR indicates that the system is highly effective at minimizing mismatches, ensuring a more accurate and reliable facial recognition process.
What Are Facial Liveness Detection Algorithms?
In remote identification, liveness detection algorithms are essential technologies that help prevent spoofing by verifying whether a person is genuinely present. These algorithms are designed to prevent fraud attempts, such as using photos, videos, or other deceptive methods. Liveness detection is performed using two primary approaches: active and passive.
Active Liveness Detection
In this method, the user is prompted to perform specific actions, such as blinking, turning their head, or making a facial expression. These actions help verify the user's presence in real-time, though they can sometimes be less user-friendly.
Passive Liveness Detection
With this approach, the user does not need to perform any action. The algorithm monitors user behavior in the background and detects liveness through biometric data such as facial features, light, depth, and skin texture. This method is preferred for its seamless integration into the user experience.
Hybrid Liveness Detection
Hybrid liveness detection combines both active and passive methods for enhanced security. By leveraging deep learning algorithms and advanced image processing techniques, this approach creates a multi-layered defense against fraud. It is particularly suitable for high-security applications, minimizing fraud risks while enhancing user identity verification reliability.
Liveness Detection (PAD) levels measure the robustness of biometric systems against spoofing attempts. Level 1 focuses on basic attacks such as photos or videos, while Level 2 focuses on advanced techniques like 3D masks and deepfakes.
fraud.com is one of the few manufacturers worldwide certified for PAD Level 1 and Level 2 Liveness Detection according to the ISO/IEC 30107-3 standard.
Udentify’s Liveness Detection Algorithms are certified by iBeta Labs (www.ibeta.com), based in Aurora, Colorado, USA. Click the relevant button for the test report summary.
The ISO/IEC 30107-3 standard for liveness detection sets international security levels and defines the methods used in biometric systems. Adhering to these standards ensures the effectiveness and accuracy of liveness detection algorithms in diverse scenarios. Therefore, only liveness detection algorithms that meet ISO/IEC 30107-3 performance criteria should be used.
Document Liveness Detection
Document Liveness Detection is a crucial security technology used in digital identity verification to ensure that documents are authentic and not forged. During digital account creation, users are often required to take a photo of their identity document, which must be genuine, unaltered, and physically present at the time of capture; such a document is considered "live." This technology focuses on preventing fraud by verifying document legitimacy and preventing fraudulent tactics like screen replay attacks, where documents are displayed from digital screens, Printed Copy Attacks, where copied documents are presented as originals, Portrait Substitution or Overlay Attacks, which involve changing photos on identity documents, and injection attacks, where previously recorded images are presented as live. Document liveness detection enhances security during authentication processes, providing assurance that the information being verified is real and valid.
Voice Liveness Detection
Our voice liveness detection technology has been developed to provide advanced security in voice-based authentication processes. Our technology focuses on preventing counterfeiting and fraudulent attempts by analyzing the characteristics of live audio in detail. First, our system asks the user to say randomly generated words or phrases. This randomness prevents the use and imitation of pre-recorded sounds. When audio data is received, acoustic signatures such as the frequency spectrum of sound waves, pitch changes, and tonal dynamics are analyzed. A real voice shows natural variations in these parameters, a feature that recorded or artificial voices often cannot offer. In addition, background noises and echoes from the environment in which the sound is recorded are used to evaluate the vibrancy of the sound. These environmental sound cues play a critical role in detecting liveness, as they are not usually present in recorded sounds. Timing and delay analysis is also an important component of our system. The time correlation between the user's voice response and the system's instructions is checked, so that any artificial timing is noticed. With these comprehensive analyses, our voice liveness detection technology secures voice-based authentication processes and effectively blocks unauthorized access attempts.
Deepfake Detection
Our cutting-edge deepfake detection technology leverages Source Device Verification, a method that identifies the originating camera or device of an image. This technique uses advanced digital forensics to thoroughly examine the metadata and digital traces within media files. Each camera leaves behind distinct, device-specific traces, such as sensor noise, lens distortions, and custom software settings, acting like a fingerprint within the media. By analyzing file metadata, key details such as creation date, file format, camera model, and software versions can be validated. Since deepfakes struggle to replicate these technical traces, they can be reliably detected. Source Device Verification provides an additional layer of security, enhancing fraud prevention and making remote authentication processes more reliable.
Our NFC-Based ID Capturing Technology
Our technology fully complies with the standards set for e-passports and other electronic identity documents. These standards define the security protocols and data formats required for safe identification. When the chip in the ID functions properly, NFC-based ID capturing operations achieve a 100% success rate. This guarantees high security and accuracy in authentication processes, thanks to the reliability and effectiveness of NFC technology. A fully operational chip ensures complete and precise data reading, providing optimal performance during ID verification.
ICAO Doc 9303
This internationally recognised standard defines the technical protocols for issuing and using machine-readable travel documents (MRTDs). It outlines precise requirements for document format, data structure, and built-in security features. Our NFC-based ID capturing technology fully complies with these protocols, enabling the accurate and secure extraction of data from electronic identity documents. The system reads data using the Logical Data Structure (LDS), which defines how personal and biometric information is organised and stored within the chip, ensuring reliability and strong security throughout the verification process.
BAC (Basic Access Control)
Basic Access Control (BAC) is a security mechanism that protects the data stored in RFID chip by ensuring it can only be accessed by authorised reading devices. BAC establishes an encrypted communication channel between the ePassport and the reader, using keys generated from the passport’s machine-readable zone (MRZ). While it relies on relatively simple cryptographic methods, it provides an essential layer of protection by preventing unauthorised access to sensitive personal and biometric information during data transmission.
EAC (Extended Access Control)
EAC is an advanced access control system built on top of BAC, designed to enhance the protection of sensitive biometric data such as fingerprints and iris scans. It employs mutual authentication, meaning both the chip and the reader must verify each other before access is granted. This two-way verification process ensures that only authorised and trusted devices can retrieve highly sensitive information, significantly strengthening the security of electronic identity documents.
PA (Passive Authentication)
PA is a verification mechanism that protects the data on ePassports from forgery or manipulation. It uses digital signatures to verify the authenticity of the data stored on the chip. These signed data are issued by the regulatory authority of the document, and their validity is confirmed using a public key obtained from the same authority. PA ensures that any tampering with the data is detected, allowing the authenticity of the document to be verified. Our technology guarantees the integrity and accuracy of the data stored on the chip by fully complying with the PA protocol.
AA (Active Authentication)
AA is a security protocol designed to verify the authenticity and physical presence of the ePassport chip. This system conducts a two-way verification process to ensure the chip is genuine and not counterfeit. During this process, the chip receives a challenge message from the verifying device and generates a signature response using a unique cryptographic key. This response proves that the chip is authentic and not a fake. AA provides an enhanced level of protection, particularly against counterfeit chip manufacturing attempts, ensuring robust security for the ePassport system.
Our technology uses the AA protocol to verify the authenticity of the chip and determine its country of origin. Leveraging NFC technology, we can reliably read and authenticate data from chip-based ID documents worldwide. This ensures that authentication processes are both secure and accurate, providing reliable verification for global identity documents.
Document Liveness Detection Technology
Our Document Liveness Detection Technology is an advanced solution used to verify the authenticity of identity documents (such as passports, ID cards, driver’s licenses) presented during digital onboarding or remote ID verification processes.
The primary goal is to ensure that the submitted document is a genuine, original, and physically present item—not a reproduction, digital copy, or manipulated image. By analyzing various visual, behavioral, and sometimes contextual cues during the capture process, our technology can distinguish between legitimate documents and a wide range of sophisticated presentation or spoofing attacks.
As a result, it greatly enhances the reliability of customer identity verification, reducing the risk of fraud and impersonation in online transactions.

Attack Vectors Mitigated
Our Document Liveness Detection Technology employs advanced algorithms to detect evidence that a document presented for verification is physically present, authentic, and untampered, thereby preventing the most common and sophisticated attack methods used by fraudsters. Below are the primary types of attacks that this technology is specifically designed to detect and mitigate.
Presentation Attacks
Document Liveness Detection is capable of identifying attempts where fraudsters present an image of an identity document on a digital device—such as a high-resolution monitor, tablet, or smartphone—during the verification process. This helps to ensure that only physical documents, and not mere digital reproductions, are accepted.
Printed Copy Attacks
This technology detects and blocks the use of forged documents that have been copied, printed onto paper or plastic, and then cut to match the size and shape of a real identity document. Such attacks try to bypass verification by mimicking the physical appearance of genuine documents, but liveness detection can identify signs of reproduction such as paper texture, print patterns, or lack of security features.
Overlay Attacks
Overlay attacks involve placing a photograph or face image onto an existing identity document, sometimes physically or digitally, to impersonate another individual. Document Liveness Detection can recognize inconsistencies and anomalies introduced by such overlays, ensuring that only untampered documents are approved.
Manipulation Attacks
These attacks rely on digital manipulation techniques, where the identity document’s data or portrait is altered using graphic editing software. Common forms include changing personal details, replacing facial images, or forging security elements. The technology analyzes the document for signs of digital tampering, such as irregularities in fonts, backgrounds, or document structures that would not be present in authentic, unaltered documents.
Our OCR-Based ID Capturing Technology
Our OCR (Optical Character Recognition) technology excels in remote identification by offering the highest level of accuracy, speed, and reliability. Our system accurately recognises alphanumeric characters and symbols on identity documents, ensuring a fast verification process that enhances customer satisfaction.
Our technology works seamlessly across various types of ID cards, passports, and official documents, providing versatile applications. Furthermore, it supports the reading of IDs and passports from multiple countries, streamlining international identity verification.
Our system operates reliably under various lighting conditions and document qualities, ensuring consistent performance. Additionally, our OCR technology seamlessly handles multilingual documents, providing language-independent recognition for global identity verification. With high security and efficiency, our OCR technology stands out as a leader in identity verification.
Our OCR-based Identity Capturing Technology
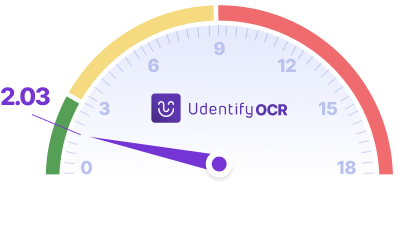
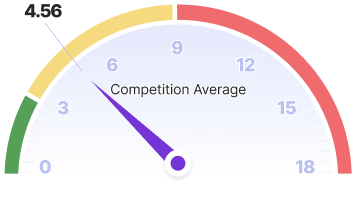
Following performance tests conducted on 403 UK Passports, our Udentify OCR Artificial Intelligence model, updated in the third quarter of 2024, achieved an impressive success rate of 94.90%. In comparison, the closest competing technology in the market only reached a success rate of 66.88%. Udentify OCR not only excels in accuracy, but also in speed, with an average processing time of just 2.03 seconds. The fastest competitor’s average processing time stands at 4.56 seconds, positioning Udentify OCR as one of the fastest solutions available in the industry.


Comparison of NFC and OCR ID Capturing
NFC and OCR ID capturing offer distinct levels of security in authentication processes. NFC ID capturing transmits data directly and encrypted from the chip in the ID card, ensuring near-100% accuracy and stronger protection against fraud. NFC technology excels in data integrity and security due to its chip-based structure. In contrast, OCR ID capturing converts text information into digital form by processing visual data from the ID. While OCR is versatile in reading a wide range of ID formats, its reliance on visual data makes it more vulnerable to fraud, especially with low-quality images or counterfeit documents. As a result, NFC reading offers superior security and fraud prevention.
Integration
Integrate Cloud KYC into your app seamlessly using our iOS and Android SDKs or the REST API. You can easily access sample code and libraries for both platforms via our developer portal. Our REST API allows you to effortlessly incorporate Cloud KYC services into your applications, with clear endpoints and data formats. To get started, generate your API keys in the Cloud KYC Dashboard. Afterward, test the integration in our environment by reviewing the sample code in the developer portal, validate your system, and activate Cloud KYC services within a fully compliant environment.
Compliant Architecture
Credentials are scanned using OCR technology through NFC or the smartphone’s camera. After capturing the identity and facial data, specialized algorithms analyze the information and compare it with real-time facial data. To meet advanced security standards, this process must be executed at the server level, as running algorithms on the client device (e.g., phone) could introduce security vulnerabilities. Biometric and identity data collected from the client using the SDK should be securely transferred to the server for processing. In line with GDPR regulations, biometric data on the server must be encrypted and protected, with encryption keys stored in a hardware security module (HSM). Additionally, it is recommended to conduct annual penetration testing to continually strengthen security protocols.
Who Needs to Be Identified?
In accordance with local regulations (add specific regulation), all organizations within the scope of financial regulatory bodies (add specific regulatory body name), including banks, payment institutions, electronic money institutions, crypto asset service providers, and electronic commerce intermediary service providers, are required to identify their customers.
What is ISO/IEC 30107-3 Level 1?
The ISO/IEC 30107-3 standard outlines criteria for fraud prevention in biometric systems, with "Level 1" forming the foundation of these requirements. Level 1 provides basic security measures for counterfeit detection, offering protection against simple attacks. For example, it defends against superficial methods like photos or basic videos used in facial recognition systems. Typically, it is ideal for low-risk applications and provides quick, practical solutions for preventing counterfeiting at a fundamental level. Systems operating at this level ensure fast transactions by adding a basic security layer that does not disrupt the user experience.
What is ISO/IEC 30107-3 Level 2?
"Level 2" of the ISO/IEC 30107-3 standard offers more advanced fraud detection capabilities for biometric systems. Level 2 is designed to safeguard against basic attacks, such as photos or videos, as well as more advanced spoofing techniques. It offers enhanced protection against sophisticated threats, including high-quality 3D masks and video manipulation. Using advanced algorithms and technologies, Level 2 delivers higher accuracy and meets more stringent security requirements, making it ideal for applications that process sensitive data.
What is Guilloche Detection?
Guilloche Detection is a technology that verifies the accuracy and authenticity of complex guilloche patterns found in identity documents. Guilloche patterns consist of intricate, intertwined lines used to enhance the security features of a document. OCR technology identifies potential counterfeiting by analyzing whether these patterns align with traditional printing methods. In the authentication process, detecting guilloche patterns effectively ensures that documents have not been tampered with or fraudulently created using graphic design software. This technology plays a crucial role in counterfeit detection.
What is Rainbow Print Detection?
Rainbow Print Detection is a technology that analyzes the rainbow printing effects found on identity documents. Rainbow printing is a technique where colors gradually shift, displaying a spectrum with subtle variations. This security feature is essential for detecting counterfeit documents. OCR technology examines the color transitions within the document to determine whether the print is authentic or fraudulent. The consistency of these color transitions is critical in verifying the document’s legitimacy, making this detection method vital for accurate authentication.
What is Optical Ink Detection?
Optical Ink Detection is an advanced technology that identifies special optical inks used in identity documents. These inks can change color or appearance when exposed to certain types of light, providing an additional layer of security against fraudulent activities. OCR technology detects these inks' presence and effectiveness, ensuring that the document remains secure and resistant to forgery. Optical ink detection verifies the authenticity of signatures and unique markings on documents, helping to identify whether they have been altered or manipulated. This technology plays a crucial role in maintaining the integrity and security standards of original documents.
What is Hidden Image Detection?
Hidden Image Detection is a technology designed to reveal and verify concealed images in identity documents, which are visible only under specific lighting conditions or angles. These hidden images enhance document security and help prevent forgery. OCR technology plays a key role in detecting identity fraud by evaluating the presence and accuracy of these hidden features. This detection method adds an extra layer of verification, ensuring document authenticity and increasing the accuracy of identity checks by identifying security elements that are not visible to the naked eye.
What is Hologram Detection?
Hologram Detection is a technology that verifies the accuracy and integrity of holographic images found in identity documents. Holograms are three-dimensional images used as a security feature to make documents more resistant to forgery. OCR technology analyzes how holograms appear under different lighting conditions and how they change when the document is moved. This process verifies the authenticity of the holograms by examining specific patterns and color gradients. By detecting counterfeit documents, hologram detection plays a crucial role in maintaining high security standards in identity verification.
What is Micro Writing Detection?
Micro Writing Detection is a technology used to detect the presence and accuracy of microwriting on identity documents, which is often invisible to the naked eye. Microwriting consists of small text elements embedded to enhance document security and prevent counterfeiting. OCR technology analyzes the clarity, content, and precision of these microtexts to verify the authenticity of the document. By focusing on details such as font type, size, and placement, this detection method adds an essential layer of security, making it significantly harder for counterfeiters to replicate these features and forge documents.
FAQ
KYC is the abbreviation for “Know Your Customer”. It is a process used by financial institutions and other specific sectors to verify the identities of their customers and understand their risk profiles. KYC is critically important not only for ensuring compliance with legal regulations but also for protecting the security and reputation of businesses.
Cloud KYC is a comprehensive cloud-based solution designed to help businesses digitize and automate their Know Your Customer (KYC) and remote identity verification processes. It provides a fully compliant, fast, secure, and user-friendly KYC experience. Cloud KYC delivers an end-to-end solution encompassing e-KYC (automated identity verification), Video KYC (verification via video call), and mobile application solutions.
The standout key features of Cloud KYC include:
Full Regulatory Compliance: Adherence to global and regional regulations including FATF AML/CTF standards, GDPR, eIDAS, SEC, FinCEN, FCA, PRA, EBA, ESMA, and relevant national FIU requirements.
Advanced Technologies: Leverages state-of-the-art technologies including NFC, OCR, Biometric Verification, Liveness Detection, and Deepfake Detection.
Video KYC and Operator Service: Identity verification via video call, with optional 24/7 operator support service.
Mobile KYC Application: Ready-to-use iOS and Android mobile application for easy deployment.
HDR Finance Cloud Infrastructure: Hosted on the high-security and regulation-compliant HDR Finance Cloud infrastructure.
Broad Integration Options: Easy integration via iOS and Android SDKs and REST API.
Additional Security Features: Includes Geolocation, List Management, S3 Storage Support, Energy Monitoring, and NFC Locator.
High Performance: Fast processing times and high accuracy rates, particularly with NFC and OCR technologies.
Scalability and Flexibility: Offers various packages suitable for different needs and a scalable infrastructure.
Technical Support: Provides comprehensive technical support and a dedicated developer portal.
Our Cloud KYC product is meticulously designed to maintain the highest level of data security while ensuring full compliance with all relevant regulations in the global financial sector. This dual focus guarantees the security of both your business and your customers, ensuring you meet all legal obligations comprehensively. Here’s a breakdown of how Cloud KYC achieves this balance:
Our Data Security-Focused Approach:
HDR Finance Cloud Infrastructure: Your data is stored within the HDR Finance Cloud infrastructure, hosted in the highly secure Credit Bureau Anadolu Data Center. This infrastructure is specifically built considering the sensitivities of the financial sector and complies with the stringent standards set by regulatory bodies such as the SEC and FinCEN in the U.S., the FCA and PRA in the UK, and the EBA and ESMA across Europe. This forms the foundation of your data security and is the first step towards regulatory compliance.
Data Encryption: In Cloud KYC, all data, both in-transit and at-rest, is protected using robust encryption algorithms. This meets the data security standards required by regulations like the EU’s GDPR and other relevant data protection laws. Customer identity information, biometric data, and all sensitive details are encrypted to prevent unauthorized access.
Hardware Security Module (HSM): Encryption keys are securely stored within a Hardware Security Module (HSM). An HSM is specialized hardware equipped with physical and logical security measures to protect encryption keys from unauthorized access, meeting regulatory expectations for sensitive data management.
Advanced Security Layers: Cloud KYC incorporates various advanced security layers, including SSL pinning, device fingerprinting, data masking, and anti-tampering techniques. These layers provide additional protection against man-in-the-middle attacks, reverse engineering attempts, and other cyber threats, further supporting regulatory requirements.
Penetration Testing: Our system security is continuously audited and improved through regular penetration tests conducted by independent security experts. This proactive approach ensures that our security standards consistently meet and exceed the evolving expectations of regulatory frameworks.
Data Center Security: The HDR Finance Cloud data centers are equipped with comprehensive physical security (24/7 security personnel, controlled access), environmental security (redundant power, climate control, fire suppression systems), and cybersecurity measures. These extensive security protocols underpin both your data security and your regulatory compliance.
Our Compliance-Focused Approach:
Compliance with Key Financial Regulations & Data Protection Laws: Our Cloud KYC product has been developed for full compliance with key financial sector regulations globally, including those enforced by the SEC, FinCEN, FCA, PRA, EBA, ESMA, and national FIUs, as well as data protection laws like the EU’s GDPR. Our processes and infrastructure meet the standards set by these bodies and are regularly updated.
Adaptation to International Standards: Compliance is not limited to specific regions. Cloud KYC is also adapted to meet international KYC and AML (Anti-Money Laundering) / CTF (Counter-Terrorism Financing) standards, guided by frameworks like those set by the FATF (Financial Action Task Force). This is crucial for businesses operating globally or serving international customers.
Continuous Updates and Monitoring: Regulations are constantly evolving. The Cloud KYC team closely monitors legislative changes and rapidly adapts our system and processes accordingly. This ensures we always offer a solution that complies with the latest regulations.
Ease of Audit and Reporting: Our Cloud KYC product provides detailed logs and reporting tools that facilitate audit processes. This makes it easier for you to demonstrate your compliance and cooperate effectively with regulatory authorities.
Cloud KYC provides businesses with the following significant advantages:
Cost Savings: Reduces operational costs, ensuring time and resource efficiency.
Faster Customer Onboarding: Accelerates customer acquisition processes and increases conversion rates.
Enhanced Security: Mitigates fraud risk, increasing security for both the customer and the business.
Ease of Regulatory Compliance: Simplifies the fulfillment of legal obligations and minimizes risks.
Improved Customer Experience: Offers easy, fast, and user-friendly KYC processes, boosting customer satisfaction.
Competitive Advantage: Provides a market edge through technological and secure KYC solutions.
Scalability and Flexibility: Easily scales as the business grows and needs evolve.
Yes, we offer a 30-day free trial for our Cloud KYC product. With the free trial, you can test our Cloud KYC platform, experience its features, and evaluate its suitability for your business.
The primary purposes of KYC are:
Legal Compliance: To comply with legal regulations aimed at preventing money laundering (AML), terrorist financing (TF/CTF), and other financial crimes (e.g., adhering to AML/CTF laws).
Fraud Prevention: To reduce forgery and fraud attempts by verifying customer identities.
Risk Management: To help businesses manage their risks by determining customer risk profiles.
Customer Protection: To contribute to protecting customers against the misuse of the financial system.
Protecting Business Reputation: To strengthen the business’s reputation by demonstrating lawful and ethical business practices.
KYC provides the following benefits to businesses and customers:
Reduced Fraud Risk: Through identity verification processes, fake identities and fraudulent activities can be detected.
Enhanced Legal Compliance: Compliance with legal regulations helps avoid fines and legal issues.
Better Risk Management: Understanding customer risk profiles enables businesses to manage their risks more effectively.
Increased Customer Trust: Secure and transparent processes enhance customer trust and support long-term customer relationships.
Global: Compliance is guided by international standards such as those established by the Financial Action Task Force (FATF), which sets comprehensive recommendations to combat money laundering and terrorist financing.
United Kingdom: Regulations include the Money Laundering, Terrorist Financing and Transfer of Funds Regulations, with oversight by the Financial Conduct Authority (FCA).
USA: Adheres to the Customer Identification Program (CIP) requirements mandated under the USA PATRIOT Act, ensuring robust verification measures.
Europe: Aligns with the EU Anti-Money Laundering Directives, notably the 4th, 5th, and the upcoming 6th AML Directives, which provide a harmonized framework for identity verification across member states.
Thanks to these thorough checks, Video KYC is as secure as in-person identity verification, ensuring customers are verified securely and reliably.
Yes, the use of KYC is legally mandatory in specific sectors. This is particularly true for the financial sector (including banks, payment institutions, crypto-asset service providers, etc.) and other entities subject to anti-money laundering (AML) and counter-terrorism financing (CTF) regulations worldwide. KYC processes are mandated by specific legal and regulatory frameworks (such as the Bank Secrecy Act/USA PATRIOT Act in the US, the EU’s Anti-Money Laundering Directives, and regulations overseen by bodies like the FCA in the UK). These organizations are required to identify their customers and fulfill their legal compliance obligations.
In addition to being a legal requirement in some cases, KYC is beneficial for many sectors. The main sectors where it is particularly applicable include:
Financial Sector: Banks, credit institutions, investment firms, insurance companies, payment and electronic money institutions, crypto-asset service providers.
E-commerce: Especially e-commerce platforms selling high-value products or services and those with high volumes of financial transactions.
Gaming and Betting Sector: Online gaming and betting platforms, primarily to prevent money laundering and ensure age verification.
Telecommunications: Telecommunication companies offering subscription services.
Rental and Real Estate: Businesses involved in the sale or rental of high-value assets.
Healthcare Sector: Particularly healthcare platforms that process sensitive data and offer online services.
The primary reasons businesses need a KYC solution are:
To Fulfill Legal Obligations: To meet the mandatory KYC requirements set by regulatory authorities (e.g., FinCEN, FCA, ESMA, national FIUs, adhering to frameworks like FATF standards).
To Combat Fraud and Financial Crime: To protect the business and its customers from risks such as fraud, money laundering, and the financing of terrorism.
To Increase Operational Efficiency: To enhance efficiency through automated and digital KYC solutions, as manual KYC processes are often time-consuming and costly.
To Improve Customer Experience: Remote and fast KYC processes increase customer satisfaction and simplify customer acquisition procedures.
To Gain a Competitive Advantage: To stand out from the competition and become a preferred choice for customers by offering secure and swift KYC processes.
Key considerations in KYC processes include:
Regulatory Compliance: Ensuring processes are fully compliant with legal regulations (e.g., AML/CTF regulations, data protection laws like GDPR).
Security: Ensuring the security of customer data through data encryption and robust security protocols.
User Experience: Making processes simple, understandable, and user-friendly to enhance customer satisfaction.
Accuracy and Speed: Performing identity verification processes accurately and quickly.
Privacy: Protecting the confidentiality of customer data and acting in accordance with data protection principles (like GDPR).
Remote identity verification is the digital implementation of traditional KYC processes. It is the verification of customers’ identities via the internet or mobile applications, without the need for them to be physically present at a location. This process typically utilizes images of identity documents (such as ID cards, passports, etc.), biometric data (like facial recognition), and liveness detection technologies.
Remote identity verification offers numerous advantages over traditional methods:
Speed and Convenience: Saves time for both customers and businesses; transactions are completed quickly and easily.
Cost Reduction: Reduces operational costs as physical branch visits are not required.
Wider Reach and Accessibility: Eliminates geographical limitations, making it possible to reach and serve a broader customer base.
Improved Customer Experience: Digital and user-friendly processes enhance customer satisfaction.
Enhanced Security and Efficiency: Advanced technologies (like NFC, OCR, biometric verification, liveness detection) increase security and accuracy, reducing manual errors.
24/7 Availability: Offers customers the ability to verify their identity at any time, any day of the week.
The primary technologies used for remote identity verification include:
NFC (Near Field Communication): Reading data directly from the chip in identity cards.
OCR (Optical Character Recognition): Optically recognizing text and visual data on the identity document.
Biometric Verification (Facial Recognition): Identity verification using facial matching algorithms.
Liveness Detection: Verifying the person’s liveness to prevent spoofing and fraud.
Video KYC: Identity verification conducted via video call with the assistance of a customer representative.
Geolocation: Enhancing security by utilizing IP address and location data.
Video KYC works as follows:
The customer initiates a video call either when experiencing issues during the standard identity verification process or by choosing the Video KYC option directly.
The customer connects to an appropriate customer representative, often guided or assigned by the system.
The customer representative guides the customer throughout the process, asks them to display their identity documents, and performs accuracy checks (inspecting visual security features, holograms, microtext, etc.).
During the video call, the customer representative guides the customer through the biometric verification and liveness detection steps.
The identity verification process is completed, and the result is communicated to the customer.
The advantages of Video KYC include:
Comprehensive Support: Provides a human-assisted solution in situations where automated systems may not suffice.
Accessibility for Diverse Users: Suitable for users with disabilities or those less comfortable with technology, reaching a broader audience through video calls.
Higher Success Rate: Increases the identity verification success rate thanks to guidance from a customer representative.
Trust and Personal Interaction: Video calls enhance customer trust and offer a more personal experience.
Regulatory Compliance: Ensures the process is securely recorded in accordance with regulations and offers a secure verification method.
Optional 24/7 Operator Service: Provides an option for continuous 24/7 operator service for businesses facing human resource constraints.
NFC (Near Field Communication) is a technology that enables wireless data communication over short distances. In KYC, it is used to read data securely and quickly from the chips embedded in identity documents (especially new-generation chipped identity cards and e-passports). NFC is preferred because it provides high security and accuracy.
The NFC identity verification process typically involves these steps:
The user holds their NFC-enabled smartphone near the NFC chip location on their identity document (e.g., ID card or e-passport).
A secure connection is established between the smartphone and the chip.
The identity and biometric data stored on the chip are transferred securely encrypted to the smartphone.
The system verifies the authenticity of the document by validating the digital signature associated with the data on the chip.
The identity verification process is completed.
The OCR identity verification process typically involves these steps:
The user captures an image of the identity document using their smartphone’s camera.
The OCR software scans the text and visual information from the image and converts it into a digital format.
The system analyzes the OCR-extracted information, checks the document’s security features (such as guilloche patterns, holograms, etc.), and verifies data integrity.
The identity verification process is completed.























